mirror of
https://github.com/kanidm/kanidm.git
synced 2025-06-05 15:47:46 +02:00
1399 cleanup cli docs (#1413)
* Cleanup cli args * Update book * Update wasm * making the CI happy --------- Co-authored-by: James Hodgkinson <james@terminaloutcomes.com>
This commit is contained in:
parent
00cca81012
commit
e33beea89d
.github
dependabot.yml
Cargo.tomlMakefileworkflows
book
book.toml
src
examples
libs
platform/debian
proto/src
rlm_python
scripts
server
tools
12
.github/dependabot.yml
vendored
12
.github/dependabot.yml
vendored
|
|
@ -2,7 +2,7 @@
|
||||||
version: 2
|
version: 2
|
||||||
updates:
|
updates:
|
||||||
- package-ecosystem: pip
|
- package-ecosystem: pip
|
||||||
directory: "/kanidm_rlm_python"
|
directory: "/rlm_python"
|
||||||
schedule:
|
schedule:
|
||||||
interval: weekly
|
interval: weekly
|
||||||
time: "06:00"
|
time: "06:00"
|
||||||
|
|
@ -37,35 +37,35 @@ updates:
|
||||||
timezone: Australia/Brisbane
|
timezone: Australia/Brisbane
|
||||||
open-pull-requests-limit: 99
|
open-pull-requests-limit: 99
|
||||||
- package-ecosystem: cargo
|
- package-ecosystem: cargo
|
||||||
directory: "/kanidmd/idm"
|
directory: "/server/core"
|
||||||
schedule:
|
schedule:
|
||||||
interval: weekly
|
interval: weekly
|
||||||
time: "06:00"
|
time: "06:00"
|
||||||
timezone: Australia/Brisbane
|
timezone: Australia/Brisbane
|
||||||
open-pull-requests-limit: 99
|
open-pull-requests-limit: 99
|
||||||
- package-ecosystem: cargo
|
- package-ecosystem: cargo
|
||||||
directory: "/kanidmd/score"
|
directory: "/server/score"
|
||||||
schedule:
|
schedule:
|
||||||
interval: weekly
|
interval: weekly
|
||||||
time: "06:00"
|
time: "06:00"
|
||||||
timezone: Australia/Brisbane
|
timezone: Australia/Brisbane
|
||||||
open-pull-requests-limit: 99
|
open-pull-requests-limit: 99
|
||||||
- package-ecosystem: cargo
|
- package-ecosystem: cargo
|
||||||
directory: "/kanidmd/daemon"
|
directory: "/server/daemon"
|
||||||
schedule:
|
schedule:
|
||||||
interval: weekly
|
interval: weekly
|
||||||
time: "06:00"
|
time: "06:00"
|
||||||
timezone: Australia/Brisbane
|
timezone: Australia/Brisbane
|
||||||
open-pull-requests-limit: 99
|
open-pull-requests-limit: 99
|
||||||
- package-ecosystem: cargo
|
- package-ecosystem: cargo
|
||||||
directory: "/kanidm_tools"
|
directory: "/tools/cli"
|
||||||
schedule:
|
schedule:
|
||||||
interval: weekly
|
interval: weekly
|
||||||
time: "06:00"
|
time: "06:00"
|
||||||
timezone: Australia/Brisbane
|
timezone: Australia/Brisbane
|
||||||
open-pull-requests-limit: 99
|
open-pull-requests-limit: 99
|
||||||
- package-ecosystem: cargo
|
- package-ecosystem: cargo
|
||||||
directory: "/kanidmd_web_ui"
|
directory: "/server/web_ui"
|
||||||
schedule:
|
schedule:
|
||||||
interval: weekly
|
interval: weekly
|
||||||
time: "06:00"
|
time: "06:00"
|
||||||
|
|
|
||||||
2
.github/workflows/docker_build_kanidm.yml
vendored
2
.github/workflows/docker_build_kanidm.yml
vendored
|
|
@ -43,4 +43,4 @@ jobs:
|
||||||
build-args: |
|
build-args: |
|
||||||
"KANIDM_FEATURES="
|
"KANIDM_FEATURES="
|
||||||
# "KANIDM_BUILD_OPTIONS=-j1"
|
# "KANIDM_BUILD_OPTIONS=-j1"
|
||||||
file: kanidm_tools/Dockerfile
|
file: tools/Dockerfile
|
||||||
|
|
|
||||||
2
.github/workflows/docker_build_kanidmd.yml
vendored
2
.github/workflows/docker_build_kanidmd.yml
vendored
|
|
@ -42,4 +42,4 @@ jobs:
|
||||||
tags: ghcr.io/kanidm/kanidmd:devel
|
tags: ghcr.io/kanidm/kanidmd:devel
|
||||||
# build-args: |
|
# build-args: |
|
||||||
# "KANIDM_BUILD_OPTIONS=-j1"
|
# "KANIDM_BUILD_OPTIONS=-j1"
|
||||||
file: kanidmd/Dockerfile
|
file: server/Dockerfile
|
||||||
|
|
|
||||||
2
.github/workflows/docker_build_radiusd.yml
vendored
2
.github/workflows/docker_build_radiusd.yml
vendored
|
|
@ -41,4 +41,4 @@ jobs:
|
||||||
# https://github.com/docker/build-push-action/issues/254
|
# https://github.com/docker/build-push-action/issues/254
|
||||||
tags: ghcr.io/kanidm/radius:devel
|
tags: ghcr.io/kanidm/radius:devel
|
||||||
context: .
|
context: .
|
||||||
file: kanidm_rlm_python/Dockerfile
|
file: rlm_python/Dockerfile
|
||||||
|
|
|
||||||
4
.github/workflows/kanidm_book.yml
vendored
4
.github/workflows/kanidm_book.yml
vendored
|
|
@ -49,9 +49,7 @@ jobs:
|
||||||
args: mdbook-template
|
args: mdbook-template
|
||||||
|
|
||||||
- name: Make all the books
|
- name: Make all the books
|
||||||
run: |
|
run: ./scripts/build_all_the_docs.sh
|
||||||
export
|
|
||||||
./build_all_the_docs.sh
|
|
||||||
|
|
||||||
- name: Install python 3.10
|
- name: Install python 3.10
|
||||||
uses: actions/setup-python@v4
|
uses: actions/setup-python@v4
|
||||||
|
|
|
||||||
|
|
@ -62,7 +62,7 @@ fernet = "^0.2.0"
|
||||||
filetime = "^0.2.20"
|
filetime = "^0.2.20"
|
||||||
futures = "^0.3.25"
|
futures = "^0.3.25"
|
||||||
futures-concurrency = "^3.1.0"
|
futures-concurrency = "^3.1.0"
|
||||||
futures-util = "^0.3.21"
|
futures-util = { version = "^0.3.21", features = ["sink"] }
|
||||||
gloo = "^0.8.0"
|
gloo = "^0.8.0"
|
||||||
gloo-net = "0.2.6"
|
gloo-net = "0.2.6"
|
||||||
hashbrown = { version = "0.12.3", features = ["serde", "inline-more", "ahash"] }
|
hashbrown = { version = "0.12.3", features = ["serde", "inline-more", "ahash"] }
|
||||||
|
|
|
||||||
44
Makefile
44
Makefile
|
|
@ -14,22 +14,12 @@ BOOK_VERSION ?= master
|
||||||
help:
|
help:
|
||||||
@grep -E -h '\s##\s' $(MAKEFILE_LIST) | sort | awk 'BEGIN {FS = ":.*?## "}; {printf "\033[36m%-20s\033[0m %s\n", $$1, $$2}'
|
@grep -E -h '\s##\s' $(MAKEFILE_LIST) | sort | awk 'BEGIN {FS = ":.*?## "}; {printf "\033[36m%-20s\033[0m %s\n", $$1, $$2}'
|
||||||
|
|
||||||
.PHONY: buildx/kanidmd/x86_64_v3
|
|
||||||
buildx/kanidmd/x86_64_v3: ## build multiarch server images
|
|
||||||
buildx/kanidmd/x86_64_v3:
|
|
||||||
@$(CONTAINER_TOOL) buildx build $(CONTAINER_TOOL_ARGS) --pull --push --platform "linux/amd64/v3" \
|
|
||||||
-f kanidmd/Dockerfile -t $(IMAGE_BASE)/server:x86_64_$(IMAGE_VERSION) \
|
|
||||||
--progress $(BUILDKIT_PROGRESS) \
|
|
||||||
--build-arg "KANIDM_BUILD_PROFILE=container_x86_64_v3" \
|
|
||||||
--build-arg "KANIDM_FEATURES=" \
|
|
||||||
$(CONTAINER_BUILD_ARGS) .
|
|
||||||
|
|
||||||
.PHONY: buildx/kanidmd
|
.PHONY: buildx/kanidmd
|
||||||
buildx/kanidmd: ## Build multiarch kanidm server images and push to docker hub
|
buildx/kanidmd: ## Build multiarch kanidm server images and push to docker hub
|
||||||
buildx/kanidmd:
|
buildx/kanidmd:
|
||||||
@$(CONTAINER_TOOL) buildx build $(CONTAINER_TOOL_ARGS) \
|
@$(CONTAINER_TOOL) buildx build $(CONTAINER_TOOL_ARGS) \
|
||||||
--pull --push --platform $(IMAGE_ARCH) \
|
--pull --push --platform $(IMAGE_ARCH) \
|
||||||
-f kanidmd/Dockerfile \
|
-f server/Dockerfile \
|
||||||
-t $(IMAGE_BASE)/server:$(IMAGE_VERSION) \
|
-t $(IMAGE_BASE)/server:$(IMAGE_VERSION) \
|
||||||
--progress $(BUILDKIT_PROGRESS) \
|
--progress $(BUILDKIT_PROGRESS) \
|
||||||
--build-arg "KANIDM_BUILD_PROFILE=container_generic" \
|
--build-arg "KANIDM_BUILD_PROFILE=container_generic" \
|
||||||
|
|
@ -41,7 +31,7 @@ buildx/kanidm_tools: ## Build multiarch kanidm tool images and push to docker hu
|
||||||
buildx/kanidm_tools:
|
buildx/kanidm_tools:
|
||||||
@$(CONTAINER_TOOL) buildx build $(CONTAINER_TOOL_ARGS) \
|
@$(CONTAINER_TOOL) buildx build $(CONTAINER_TOOL_ARGS) \
|
||||||
--pull --push --platform $(IMAGE_ARCH) \
|
--pull --push --platform $(IMAGE_ARCH) \
|
||||||
-f kanidm_tools/Dockerfile \
|
-f tools/Dockerfile \
|
||||||
-t $(IMAGE_BASE)/tools:$(IMAGE_VERSION) \
|
-t $(IMAGE_BASE)/tools:$(IMAGE_VERSION) \
|
||||||
--progress $(BUILDKIT_PROGRESS) \
|
--progress $(BUILDKIT_PROGRESS) \
|
||||||
--build-arg "KANIDM_BUILD_PROFILE=container_generic" \
|
--build-arg "KANIDM_BUILD_PROFILE=container_generic" \
|
||||||
|
|
@ -53,17 +43,17 @@ buildx/radiusd: ## Build multi-arch radius docker images and push to docker hub
|
||||||
buildx/radiusd:
|
buildx/radiusd:
|
||||||
@$(CONTAINER_TOOL) buildx build $(CONTAINER_TOOL_ARGS) \
|
@$(CONTAINER_TOOL) buildx build $(CONTAINER_TOOL_ARGS) \
|
||||||
--pull --push --platform $(IMAGE_ARCH) \
|
--pull --push --platform $(IMAGE_ARCH) \
|
||||||
-f kanidm_rlm_python/Dockerfile \
|
-f rlm_python/Dockerfile \
|
||||||
--progress $(BUILDKIT_PROGRESS) \
|
--progress $(BUILDKIT_PROGRESS) \
|
||||||
-t $(IMAGE_BASE)/radius:$(IMAGE_VERSION) .
|
-t $(IMAGE_BASE)/radius:$(IMAGE_VERSION) .
|
||||||
|
|
||||||
.PHONY: buildx
|
.PHONY: buildx
|
||||||
buildx: buildx/kanidmd/x86_64_v3 buildx/kanidmd buildx/kanidm_tools buildx/radiusd
|
buildx: buildx/kanidmd buildx/kanidm_tools buildx/radiusd
|
||||||
|
|
||||||
.PHONY: build/kanidmd
|
.PHONY: build/kanidmd
|
||||||
build/kanidmd: ## Build the kanidmd docker image locally
|
build/kanidmd: ## Build the kanidmd docker image locally
|
||||||
build/kanidmd:
|
build/kanidmd:
|
||||||
@$(CONTAINER_TOOL) build $(CONTAINER_TOOL_ARGS) -f kanidmd/Dockerfile -t $(IMAGE_BASE)/server:$(IMAGE_VERSION) \
|
@$(CONTAINER_TOOL) build $(CONTAINER_TOOL_ARGS) -f server/Dockerfile -t $(IMAGE_BASE)/server:$(IMAGE_VERSION) \
|
||||||
--build-arg "KANIDM_BUILD_PROFILE=container_generic" \
|
--build-arg "KANIDM_BUILD_PROFILE=container_generic" \
|
||||||
--build-arg "KANIDM_FEATURES=" \
|
--build-arg "KANIDM_FEATURES=" \
|
||||||
$(CONTAINER_BUILD_ARGS) .
|
$(CONTAINER_BUILD_ARGS) .
|
||||||
|
|
@ -72,7 +62,7 @@ build/kanidmd:
|
||||||
build/radiusd: ## Build the radiusd docker image locally
|
build/radiusd: ## Build the radiusd docker image locally
|
||||||
build/radiusd:
|
build/radiusd:
|
||||||
@$(CONTAINER_TOOL) build $(CONTAINER_TOOL_ARGS) \
|
@$(CONTAINER_TOOL) build $(CONTAINER_TOOL_ARGS) \
|
||||||
-f kanidm_rlm_python/Dockerfile \
|
-f rlm_python/Dockerfile \
|
||||||
-t $(IMAGE_BASE)/radius:$(IMAGE_VERSION) .
|
-t $(IMAGE_BASE)/radius:$(IMAGE_VERSION) .
|
||||||
|
|
||||||
.PHONY: build
|
.PHONY: build
|
||||||
|
|
@ -82,7 +72,7 @@ build: build/kanidmd build/radiusd
|
||||||
test/kanidmd: ## Run cargo test in docker
|
test/kanidmd: ## Run cargo test in docker
|
||||||
test/kanidmd:
|
test/kanidmd:
|
||||||
@$(CONTAINER_TOOL) build \
|
@$(CONTAINER_TOOL) build \
|
||||||
$(CONTAINER_TOOL_ARGS) -f kanidmd/Dockerfile \
|
$(CONTAINER_TOOL_ARGS) -f server/Dockerfile \
|
||||||
--target builder \
|
--target builder \
|
||||||
-t $(IMAGE_BASE)/server:$(IMAGE_VERSION)-builder \
|
-t $(IMAGE_BASE)/server:$(IMAGE_VERSION)-builder \
|
||||||
$(CONTAINER_BUILD_ARGS) .
|
$(CONTAINER_BUILD_ARGS) .
|
||||||
|
|
@ -91,7 +81,7 @@ test/kanidmd:
|
||||||
.PHONY: test/radiusd
|
.PHONY: test/radiusd
|
||||||
test/radiusd: ## Run a test radius server
|
test/radiusd: ## Run a test radius server
|
||||||
test/radiusd: build/radiusd
|
test/radiusd: build/radiusd
|
||||||
cd kanidm_rlm_python && \
|
cd rlm_python && \
|
||||||
./run_radius_container.sh
|
./run_radius_container.sh
|
||||||
|
|
||||||
.PHONY: test
|
.PHONY: test
|
||||||
|
|
@ -113,7 +103,7 @@ vendor-prep: vendor
|
||||||
.PHONY: install-tools
|
.PHONY: install-tools
|
||||||
install-tools: ## install kanidm_tools in your local environment
|
install-tools: ## install kanidm_tools in your local environment
|
||||||
install-tools:
|
install-tools:
|
||||||
cd kanidm_tools && cargo install --path . --force
|
cargo install --path tools/cli --force
|
||||||
|
|
||||||
.PHONY: codespell
|
.PHONY: codespell
|
||||||
codespell:
|
codespell:
|
||||||
|
|
@ -121,8 +111,8 @@ codespell:
|
||||||
-L crate,unexpect,Pres,pres,ACI,aci,te,ue \
|
-L crate,unexpect,Pres,pres,ACI,aci,te,ue \
|
||||||
--skip='./target,./pykanidm/.venv,./pykanidm/.mypy_cache,./.mypy_cache' \
|
--skip='./target,./pykanidm/.venv,./pykanidm/.mypy_cache,./.mypy_cache' \
|
||||||
--skip='./docs/*,./.git' \
|
--skip='./docs/*,./.git' \
|
||||||
--skip='./kanidmd_web_ui/src/external,./kanidmd_web_ui/pkg/external' \
|
--skip='./server/web_ui/src/external,./server/web_ui/pkg/external' \
|
||||||
--skip='./kanidmd/lib/src/constants/system_config.rs,./pykanidm/site,./kanidmd/lib/src/constants/*.json'
|
--skip='./server/lib/src/constants/system_config.rs,./pykanidm/site,./server/lib/src/constants/*.json'
|
||||||
|
|
||||||
.PHONY: test/pykanidm/pytest
|
.PHONY: test/pykanidm/pytest
|
||||||
test/pykanidm/pytest: ## python library testing
|
test/pykanidm/pytest: ## python library testing
|
||||||
|
|
@ -170,9 +160,9 @@ doc/format/fix: ## Fix docs and the Kanidm book
|
||||||
book: ## Build the Kanidm book
|
book: ## Build the Kanidm book
|
||||||
book:
|
book:
|
||||||
cargo doc --no-deps
|
cargo doc --no-deps
|
||||||
mdbook build kanidm_book
|
mdbook build book
|
||||||
rm -rf ./docs/
|
rm -rf ./docs/
|
||||||
mv ./kanidm_book/book/ ./docs/
|
mv ./book/book/ ./docs/
|
||||||
mkdir -p ./docs/rustdoc/${BOOK_VERSION}
|
mkdir -p ./docs/rustdoc/${BOOK_VERSION}
|
||||||
mv ./target/doc/* ./docs/rustdoc/${BOOK_VERSION}/
|
mv ./target/doc/* ./docs/rustdoc/${BOOK_VERSION}/
|
||||||
|
|
||||||
|
|
@ -183,10 +173,10 @@ book_versioned:
|
||||||
git switch -c "${BOOK_VERSION}"
|
git switch -c "${BOOK_VERSION}"
|
||||||
git pull origin "${BOOK_VERSION}"
|
git pull origin "${BOOK_VERSION}"
|
||||||
cargo doc --no-deps --quiet
|
cargo doc --no-deps --quiet
|
||||||
mdbook build kanidm_book
|
mdbook build book
|
||||||
rm -rf ./docs/
|
rm -rf ./docs/
|
||||||
mkdir -p ./docs
|
mkdir -p ./docs
|
||||||
mv ./kanidm_book/book/ ./docs/${BOOK_VERSION}/
|
mv ./book/book/ ./docs/${BOOK_VERSION}/
|
||||||
mkdir -p ./docs/${BOOK_VERSION}/rustdoc/
|
mkdir -p ./docs/${BOOK_VERSION}/rustdoc/
|
||||||
mv ./target/doc/* ./docs/${BOOK_VERSION}/rustdoc/
|
mv ./target/doc/* ./docs/${BOOK_VERSION}/rustdoc/
|
||||||
git switch master
|
git switch master
|
||||||
|
|
@ -254,5 +244,5 @@ cert/clean:
|
||||||
rm -f /tmp/kanidm/ca.{cnf,srl,srl.old}
|
rm -f /tmp/kanidm/ca.{cnf,srl,srl.old}
|
||||||
|
|
||||||
.PHONY: webui
|
.PHONY: webui
|
||||||
webui: ## Build the WASM web frontent
|
webui: ## Build the WASM web frontend
|
||||||
cd kanidmd_web_ui && ./build_wasm_release.sh
|
cd server/web_ui && ./build_wasm_release.sh
|
||||||
|
|
|
||||||
|
|
@ -10,7 +10,7 @@ src = "src"
|
||||||
title = "Kanidm Administration"
|
title = "Kanidm Administration"
|
||||||
|
|
||||||
[output.html]
|
[output.html]
|
||||||
edit-url-template = "https://github.com/kanidm/kanidm/edit/master/kanidm_book/{path}"
|
edit-url-template = "https://github.com/kanidm/kanidm/edit/master/book/{path}"
|
||||||
git-repository-url = "https://github.com/kanidm/kanidm"
|
git-repository-url = "https://github.com/kanidm/kanidm"
|
||||||
|
|
||||||
[preprocessor.template]
|
[preprocessor.template]
|
||||||
|
|
|
||||||
|
|
@ -244,7 +244,7 @@ kanidm raw delete -H https://localhost:8443 -C ../insecure/ca.pem -D idm_admin '
|
||||||
|
|
||||||
### Building the Web UI
|
### Building the Web UI
|
||||||
|
|
||||||
**NOTE:** There is a pre-packaged version of the Web UI at `/kanidmd_web_ui/pkg/`, which can be used
|
**NOTE:** There is a pre-packaged version of the Web UI at `/server/web_ui/pkg/`, which can be used
|
||||||
directly. This means you don't need to build the Web UI yourself.
|
directly. This means you don't need to build the Web UI yourself.
|
||||||
|
|
||||||
The Web UI uses Rust WebAssembly rather than Javascript. To build this you need to set up the
|
The Web UI uses Rust WebAssembly rather than Javascript. To build this you need to set up the
|
||||||
|
|
@ -257,7 +257,7 @@ cargo install wasm-pack
|
||||||
Then you are able to build the UI:
|
Then you are able to build the UI:
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
cd kanidmd_web_ui/
|
cd server/web_ui/
|
||||||
./build_wasm_dev.sh
|
./build_wasm_dev.sh
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
@ -335,13 +335,12 @@ cargo install mdbook
|
||||||
To build it:
|
To build it:
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
cd kanidm_book
|
make book
|
||||||
mdbook build
|
|
||||||
```
|
```
|
||||||
|
|
||||||
Or to run a local webserver:
|
Or to run a local webserver:
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
cd kanidm_book
|
cd book
|
||||||
mdbook serve
|
mdbook serve
|
||||||
```
|
```
|
||||||
|
|
|
||||||
|
|
@ -5,8 +5,8 @@
|
||||||
- [Choosing a Domain Name](choosing_a_domain_name.md)
|
- [Choosing a Domain Name](choosing_a_domain_name.md)
|
||||||
- [Preparing for your Deployment](prepare_the_server.md)
|
- [Preparing for your Deployment](prepare_the_server.md)
|
||||||
- [Server Configuration and Install](server_configuration.md)
|
- [Server Configuration and Install](server_configuration.md)
|
||||||
- [Server Updates](server_update.md)
|
|
||||||
- [Platform Security Hardening](security_hardening.md)
|
- [Platform Security Hardening](security_hardening.md)
|
||||||
|
- [Server Updates](server_update.md)
|
||||||
- [Client Tools](client_tools.md)
|
- [Client Tools](client_tools.md)
|
||||||
- [Installing client tools](installing_client_tools.md)
|
- [Installing client tools](installing_client_tools.md)
|
||||||
|
|
||||||
|
|
@ -14,26 +14,21 @@
|
||||||
|
|
||||||
- [Administration](administrivia.md)
|
- [Administration](administrivia.md)
|
||||||
- [Accounts and Groups](accounts_and_groups.md)
|
- [Accounts and Groups](accounts_and_groups.md)
|
||||||
|
- [POSIX Accounts and Groups](posix_accounts.md)
|
||||||
- [Backup and Restore](backup_restore.md)
|
- [Backup and Restore](backup_restore.md)
|
||||||
- [Database Maintenance](database_maint.md)
|
- [Database Maintenance](database_maint.md)
|
||||||
- [Domain Rename](domain_rename.md)
|
- [Domain Rename](domain_rename.md)
|
||||||
- [Monitoring the platform](monitoring.md)
|
- [Monitoring the platform](monitoring.md)
|
||||||
- [Password Quality and Badlisting](password_quality.md)
|
- [Password Quality and Badlisting](password_quality.md)
|
||||||
- [POSIX Accounts and Groups](posix_accounts.md)
|
|
||||||
- [SSH Key Distribution](ssh_key_dist.md)
|
|
||||||
- [The Recycle Bin](recycle_bin.md)
|
- [The Recycle Bin](recycle_bin.md)
|
||||||
- [Troubleshooting](troubleshooting.md)
|
|
||||||
|
|
||||||
- [Frequently Asked Questions](frequently_asked_questions.md)
|
|
||||||
|
|
||||||
- [Glossary of Technical Terms](glossary.md)
|
|
||||||
|
|
||||||
# Services
|
# Services
|
||||||
|
|
||||||
- [Oauth2](integrations/oauth2.md)
|
|
||||||
- [PAM and nsswitch](integrations/pam_and_nsswitch.md)
|
- [PAM and nsswitch](integrations/pam_and_nsswitch.md)
|
||||||
- [RADIUS](integrations/radius.md)
|
- [SSH Key Distribution](ssh_key_dist.md)
|
||||||
|
- [Oauth2](integrations/oauth2.md)
|
||||||
- [LDAP](integrations/ldap.md)
|
- [LDAP](integrations/ldap.md)
|
||||||
|
- [RADIUS](integrations/radius.md)
|
||||||
|
|
||||||
# Synchronisation
|
# Synchronisation
|
||||||
|
|
||||||
|
|
@ -45,6 +40,12 @@
|
||||||
- [Kubernetes Ingress](examples/k8s_ingress_example.md)
|
- [Kubernetes Ingress](examples/k8s_ingress_example.md)
|
||||||
- [Traefik](integrations/traefik.md)
|
- [Traefik](integrations/traefik.md)
|
||||||
|
|
||||||
|
# Support
|
||||||
|
|
||||||
|
- [Troubleshooting](troubleshooting.md)
|
||||||
|
- [Frequently Asked Questions](frequently_asked_questions.md)
|
||||||
|
- [Glossary of Technical Terms](glossary.md)
|
||||||
|
|
||||||
# For Developers
|
# For Developers
|
||||||
|
|
||||||
- [Developer Guide](DEVELOPER_README.md)
|
- [Developer Guide](DEVELOPER_README.md)
|
||||||
|
|
|
||||||
|
|
@ -51,34 +51,9 @@ sensitive data), group management, and more.
|
||||||
By default the `admin` and `idm_admin` accounts have no password, and can not be accessed. They need
|
By default the `admin` and `idm_admin` accounts have no password, and can not be accessed. They need
|
||||||
to be "recovered" from the server that is running the kanidmd server.
|
to be "recovered" from the server that is running the kanidmd server.
|
||||||
|
|
||||||
<!-- deno-fmt-ignore-start -->
|
You should have already recovered the admin account during your setup process. If not refer to the
|
||||||
|
[server configuration chapter](server_configuration.md#default-admin-account) on how to recover this
|
||||||
{{#template templates/kani-warning.md
|
account.
|
||||||
imagepath=images
|
|
||||||
title=Warning!
|
|
||||||
text=The server must not be running at this point, as it requires exclusive access to the database.
|
|
||||||
}}
|
|
||||||
|
|
||||||
<!-- deno-fmt-ignore-end -->
|
|
||||||
|
|
||||||
```shell
|
|
||||||
kanidmd recover_account admin -c /etc/kanidm/server.toml
|
|
||||||
# Successfully recovered account 'admin' - password reset to -> j9YUv...
|
|
||||||
```
|
|
||||||
|
|
||||||
To do this with Docker, you'll need to stop the existing container and use the "command" argument to
|
|
||||||
access the kanidmd binary.
|
|
||||||
|
|
||||||
```bash
|
|
||||||
docker run --rm -it \
|
|
||||||
-v/tmp/kanidm:/data \
|
|
||||||
--name kanidmd \
|
|
||||||
--hostname kanidmd \
|
|
||||||
kanidm/server:latest \
|
|
||||||
kanidmd recover_account admin -c /data/server.toml
|
|
||||||
```
|
|
||||||
|
|
||||||
After the recovery is complete the server can be started again.
|
|
||||||
|
|
||||||
Once you have access to the admin account, it is able to reset the credentials of the `idm_admin`
|
Once you have access to the admin account, it is able to reset the credentials of the `idm_admin`
|
||||||
account.
|
account.
|
||||||
|
|
@ -111,8 +86,8 @@ kanidm person create demo_user "Demonstration User" --name idm_admin
|
||||||
kanidm person get demo_user --name idm_admin
|
kanidm person get demo_user --name idm_admin
|
||||||
|
|
||||||
kanidm group create demo_group --name idm_admin
|
kanidm group create demo_group --name idm_admin
|
||||||
kanidm group add_members demo_group demo_user --name idm_admin
|
kanidm group add-members demo_group demo_user --name idm_admin
|
||||||
kanidm group list_members demo_group --name idm_admin
|
kanidm group list-members demo_group --name idm_admin
|
||||||
```
|
```
|
||||||
|
|
||||||
You can also use anonymous to view accounts and groups - note that you won't see certain fields due
|
You can also use anonymous to view accounts and groups - note that you won't see certain fields due
|
||||||
|
|
@ -149,7 +124,7 @@ text=Persons may change their own displayname, name, and legal name at any time.
|
||||||
Members of the `idm_account_manage_priv` group have the rights to manage person and service accounts
|
Members of the `idm_account_manage_priv` group have the rights to manage person and service accounts
|
||||||
security and login aspects. This includes resetting account credentials.
|
security and login aspects. This includes resetting account credentials.
|
||||||
|
|
||||||
You can perform a password reset on the demo_user, for example as the idm_admin user, who is a
|
You can perform a password reset on the demo\_user, for example as the idm\_admin user, who is a
|
||||||
default member of this group. The lines below prefixed with `#` are the interactive credential
|
default member of this group. The lines below prefixed with `#` are the interactive credential
|
||||||
update interface.
|
update interface.
|
||||||
|
|
||||||
|
|
@ -268,8 +243,8 @@ An example can be easily shown with:
|
||||||
kanidm group create group_1 --name idm_admin
|
kanidm group create group_1 --name idm_admin
|
||||||
kanidm group create group_2 --name idm_admin
|
kanidm group create group_2 --name idm_admin
|
||||||
kanidm person create nest_example "Nesting Account Example" --name idm_admin
|
kanidm person create nest_example "Nesting Account Example" --name idm_admin
|
||||||
kanidm group add_members group_1 group_2 --name idm_admin
|
kanidm group add-members group_1 group_2 --name idm_admin
|
||||||
kanidm group add_members group_2 nest_example --name idm_admin
|
kanidm group add-members group_2 nest_example --name idm_admin
|
||||||
kanidm person get nest_example --name anonymous
|
kanidm person get nest_example --name anonymous
|
||||||
```
|
```
|
||||||
|
|
||||||
|
|
@ -338,42 +313,42 @@ Adding the user to the `idm_people_self_write_mail` group, as shown below, allow
|
||||||
their own mail.
|
their own mail.
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
kanidm group add_members idm_people_self_write_mail_priv demo_user --name idm_admin
|
kanidm group add-members idm_people_self_write_mail_priv demo_user --name idm_admin
|
||||||
```
|
```
|
||||||
|
|
||||||
## Why Can't I Change admin With idm_admin?
|
## Why Can't I Change admin With idm\_admin?
|
||||||
|
|
||||||
As a security mechanism there is a distinction between "accounts" and "high permission accounts".
|
As a security mechanism there is a distinction between "accounts" and "high permission accounts".
|
||||||
This is to help prevent elevation attacks, where say a member of a service desk could attempt to
|
This is to help prevent elevation attacks, where say a member of a service desk could attempt to
|
||||||
reset the password of idm_admin or admin, or even a member of HR or System Admin teams to move
|
reset the password of idm\_admin or admin, or even a member of HR or System Admin teams to move
|
||||||
laterally.
|
laterally.
|
||||||
|
|
||||||
Generally, membership of a "privilege" group that ships with Kanidm, such as:
|
Generally, membership of a "privilege" group that ships with Kanidm, such as:
|
||||||
|
|
||||||
- idm_account_manage_priv
|
- idm\_account\_manage\_priv
|
||||||
- idm_people_read_priv
|
- idm\_people\_read\_priv
|
||||||
- idm_schema_manage_priv
|
- idm\_schema\_manage\_priv
|
||||||
- many more ...
|
- many more ...
|
||||||
|
|
||||||
...indirectly grants you membership to "idm_high_privilege". If you are a member of this group, the
|
...indirectly grants you membership to "idm\_high\_privilege". If you are a member of this group,
|
||||||
standard "account" and "people" rights groups are NOT able to alter, read or manage these accounts.
|
the standard "account" and "people" rights groups are NOT able to alter, read or manage these
|
||||||
To manage these accounts higher rights are required, such as those held by the admin account are
|
accounts. To manage these accounts higher rights are required, such as those held by the admin
|
||||||
required.
|
account are required.
|
||||||
|
|
||||||
Further, groups that are considered "idm_high_privilege" can NOT be managed by the standard
|
Further, groups that are considered "idm\_high\_privilege" can NOT be managed by the standard
|
||||||
"idm_group_manage_priv" group.
|
"idm\_group\_manage\_priv" group.
|
||||||
|
|
||||||
Management of high privilege accounts and groups is granted through the the "hp" variants of all
|
Management of high privilege accounts and groups is granted through the the "hp" variants of all
|
||||||
privileges. A non-conclusive list:
|
privileges. A non-conclusive list:
|
||||||
|
|
||||||
- idm_hp_account_read_priv
|
- idm\_hp\_account\_read\_priv
|
||||||
- idm_hp_account_manage_priv
|
- idm\_hp\_account\_manage\_priv
|
||||||
- idm_hp_account_write_priv
|
- idm\_hp\_account\_write\_priv
|
||||||
- idm_hp_group_manage_priv
|
- idm\_hp\_group\_manage\_priv
|
||||||
- idm_hp_group_write_priv
|
- idm\_hp\_group\_write\_priv
|
||||||
|
|
||||||
Membership of any of these groups should be considered to be equivalent to system administration
|
Membership of any of these groups should be considered to be equivalent to system administration
|
||||||
rights in the directory, and by extension, over all network resources that trust Kanidm.
|
rights in the directory, and by extension, over all network resources that trust Kanidm.
|
||||||
|
|
||||||
All groups that are flagged as "idm_high_privilege" should be audited and monitored to ensure that
|
All groups that are flagged as "idm\_high\_privilege" should be audited and monitored to ensure that
|
||||||
they are not altered.
|
they are not altered.
|
||||||
|
|
|
||||||
BIN
book/src/images/KanidmUseCases.graffle
Normal file
BIN
book/src/images/KanidmUseCases.graffle
Normal file
Binary file not shown.
BIN
book/src/images/KanidmUseCases.png
Normal file
BIN
book/src/images/KanidmUseCases.png
Normal file
Binary file not shown.
|
After 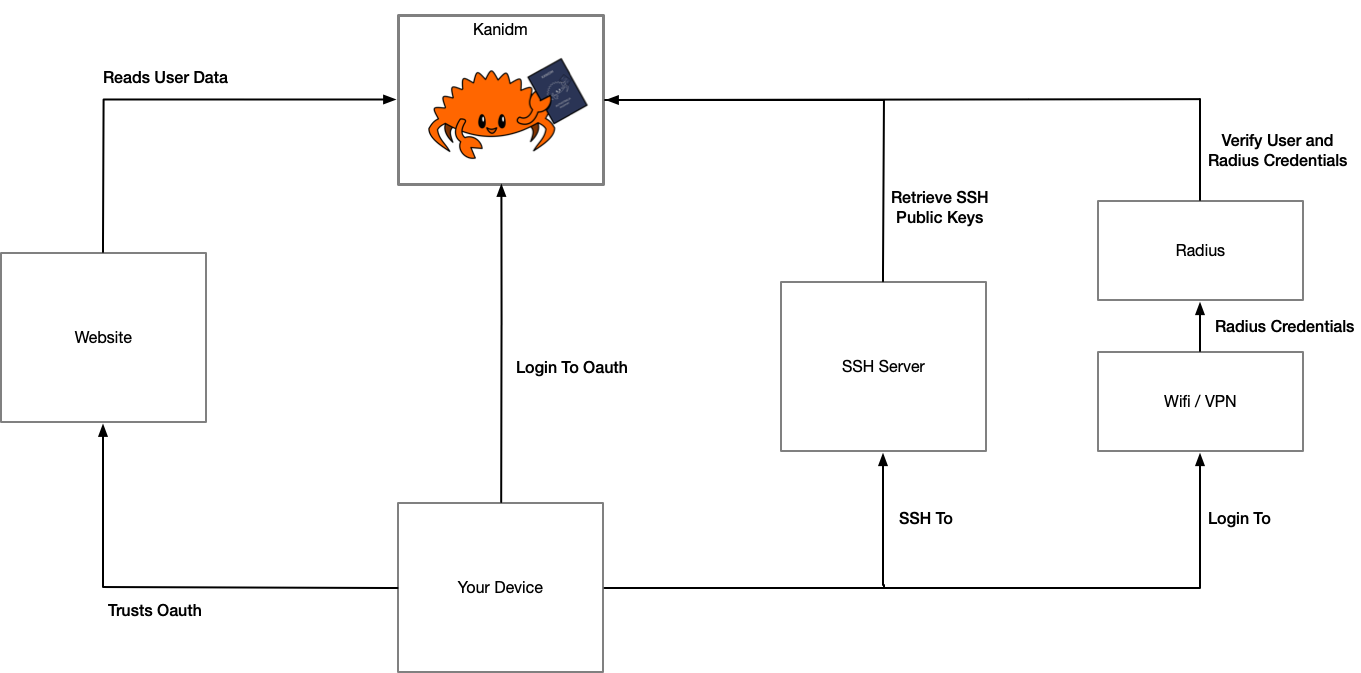
(image error) Size: 69 KiB |
|
|
@ -9,7 +9,7 @@
|
||||||
Kanidm currently is packaged for the following systems:
|
Kanidm currently is packaged for the following systems:
|
||||||
|
|
||||||
- OpenSUSE Tumbleweed
|
- OpenSUSE Tumbleweed
|
||||||
- OpenSUSE Leap 15.3/15.4
|
- OpenSUSE Leap 15.4
|
||||||
- MacOS
|
- MacOS
|
||||||
- Arch Linux
|
- Arch Linux
|
||||||
- NixOS
|
- NixOS
|
||||||
|
|
@ -92,10 +92,10 @@ dnf install kanidm-clients
|
||||||
|
|
||||||
The tools are available as a cargo download if you have a rust tool chain available. To install rust
|
The tools are available as a cargo download if you have a rust tool chain available. To install rust
|
||||||
you should follow the documentation for [rustup](https://rustup.rs/). These will be installed into
|
you should follow the documentation for [rustup](https://rustup.rs/). These will be installed into
|
||||||
your home directory. To update these, re-run the install command with the new version.
|
your home directory. To update these, re-run the install command.
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
cargo install --version 1.1.0-alpha.10 kanidm_tools
|
cargo install kanidm_tools
|
||||||
```
|
```
|
||||||
|
|
||||||
## Tools Container
|
## Tools Container
|
||||||
|
|
@ -103,9 +103,14 @@ cargo install --version 1.1.0-alpha.10 kanidm_tools
|
||||||
In some cases if your distribution does not have native kanidm-client support, and you can't access
|
In some cases if your distribution does not have native kanidm-client support, and you can't access
|
||||||
cargo for the install for some reason, you can use the cli tools from a docker container instead.
|
cargo for the install for some reason, you can use the cli tools from a docker container instead.
|
||||||
|
|
||||||
|
This really is a "last resort" and we don't really recommend this for day to day usage.
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
|
echo '{}' > ~/.cache/kanidm_tokens
|
||||||
|
chmod 666 ~/.cache/kanidm_tokens
|
||||||
docker pull kanidm/tools:latest
|
docker pull kanidm/tools:latest
|
||||||
docker run --rm -i -t \
|
docker run --rm -i -t \
|
||||||
|
--network host \
|
||||||
-v /etc/kanidm/config:/etc/kanidm/config:ro \
|
-v /etc/kanidm/config:/etc/kanidm/config:ro \
|
||||||
-v ~/.config/kanidm:/home/kanidm/.config/kanidm:ro \
|
-v ~/.config/kanidm:/home/kanidm/.config/kanidm:ro \
|
||||||
-v ~/.cache/kanidm_tokens:/home/kanidm/.cache/kanidm_tokens \
|
-v ~/.cache/kanidm_tokens:/home/kanidm/.cache/kanidm_tokens \
|
||||||
|
|
@ -113,7 +118,7 @@ docker run --rm -i -t \
|
||||||
/sbin/kanidm --help
|
/sbin/kanidm --help
|
||||||
```
|
```
|
||||||
|
|
||||||
If you have a ca.pem you may need to bind mount this in as required.
|
If you have a ca.pem you may need to bind mount this in as required as well.
|
||||||
|
|
||||||
> **TIP** You can alias the docker run command to make the tools easier to access such as:
|
> **TIP** You can alias the docker run command to make the tools easier to access such as:
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,10 +1,10 @@
|
||||||
# LDAP
|
# LDAP
|
||||||
|
|
||||||
While many applications can support external authentication and identity services through Oauth2,
|
While many applications can support external authentication and identity services through Oauth2,
|
||||||
not all services can. Lightweight Directory Access Protocol (LDAP) has been the "lingua franca" of
|
not all services can. Lightweight Directory Access Protocol (LDAP) has been the "universal language"
|
||||||
authentication for many years, with almost every application in the world being able to search and
|
of authentication for many years, with almost every application in the world being able to search
|
||||||
bind to LDAP. As many organisations still rely on LDAP, Kanidm can host a read-only LDAP interface
|
and bind to LDAP. As many organisations still rely on LDAP, Kanidm can host a read-only LDAP
|
||||||
for these legacy applications.
|
interface for these legacy applications and services.
|
||||||
|
|
||||||
<!-- deno-fmt-ignore-start -->
|
<!-- deno-fmt-ignore-start -->
|
||||||
|
|
||||||
|
|
@ -56,8 +56,7 @@ consuming applications.
|
||||||
### TLS
|
### TLS
|
||||||
|
|
||||||
StartTLS is not supported due to security risks. LDAPS is the only secure method of communicating to
|
StartTLS is not supported due to security risks. LDAPS is the only secure method of communicating to
|
||||||
any LDAP server. Kanidm, when configured with certificates, will use them for LDAPS (and will not
|
any LDAP server. Kanidm will use it's certificates for both HTTPS and LDAPS.
|
||||||
listen on a plaintext LDAP port).
|
|
||||||
|
|
||||||
### Writes
|
### Writes
|
||||||
|
|
||||||
|
|
@ -69,8 +68,8 @@ contains. As a result, writes are rejected for all users via the LDAP interface.
|
||||||
LDAP only supports password authentication. As LDAP is used heavily in POSIX environments the LDAP
|
LDAP only supports password authentication. As LDAP is used heavily in POSIX environments the LDAP
|
||||||
bind for any DN will use its configured posix password.
|
bind for any DN will use its configured posix password.
|
||||||
|
|
||||||
As the POSIX password is not equivalent in strength to the primary credentials of Kanidm (which may
|
As the POSIX password is not equivalent in strength to the primary credentials of Kanidm (which in
|
||||||
be multi-factor authentication, MFA), the LDAP bind does not grant rights to elevated read
|
most cases is multi-factor authentication), the LDAP bind does not grant rights to elevated read
|
||||||
permissions. All binds have the permissions of "Anonymous" even if the anonymous account is locked.
|
permissions. All binds have the permissions of "Anonymous" even if the anonymous account is locked.
|
||||||
|
|
||||||
The exception is service accounts which can use api-tokens during an LDAP bind for elevated read
|
The exception is service accounts which can use api-tokens during an LDAP bind for elevated read
|
||||||
|
|
|
||||||
|
|
@ -125,8 +125,8 @@ kanidm system oauth2 create nextcloud "Nextcloud Production" https://nextcloud.e
|
||||||
You can create a scope map with:
|
You can create a scope map with:
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
kanidm system oauth2 update_scope_map <name> <kanidm_group_name> [scopes]...
|
kanidm system oauth2 update-scope-map <name> <kanidm_group_name> [scopes]...
|
||||||
kanidm system oauth2 update_scope_map nextcloud nextcloud_admins admin
|
kanidm system oauth2 update-scope-map nextcloud nextcloud_admins admin
|
||||||
```
|
```
|
||||||
|
|
||||||
<!-- deno-fmt-ignore-start -->
|
<!-- deno-fmt-ignore-start -->
|
||||||
|
|
@ -153,8 +153,8 @@ text=If you are creating an OpenID Connect (OIDC) resource server you <b>MUST</b
|
||||||
You can create a supplemental scope map with:
|
You can create a supplemental scope map with:
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
kanidm system oauth2 update_sup_scope_map <name> <kanidm_group_name> [scopes]...
|
kanidm system oauth2 update-sup-scope-map <name> <kanidm_group_name> [scopes]...
|
||||||
kanidm system oauth2 update_sup_scope_map nextcloud nextcloud_admins admin
|
kanidm system oauth2 update-sup-scope-map nextcloud nextcloud_admins admin
|
||||||
```
|
```
|
||||||
|
|
||||||
Once created you can view the details of the resource server.
|
Once created you can view the details of the resource server.
|
||||||
|
|
@ -187,7 +187,7 @@ invalidate a resource servers active sessions/tokens, you can reset the secret m
|
||||||
server with:
|
server with:
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
kanidm system oauth2 reset_secrets
|
kanidm system oauth2 reset-secrets
|
||||||
```
|
```
|
||||||
|
|
||||||
Each resource server has unique signing keys and access secrets, so this is limited to each resource
|
Each resource server has unique signing keys and access secrets, so this is limited to each resource
|
||||||
|
|
@ -211,13 +211,13 @@ title=WARNING text=Changing these settings MAY have serious consequences on the
|
||||||
To disable PKCE for a resource server:
|
To disable PKCE for a resource server:
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
kanidm system oauth2 warning_insecure_client_disable_pkce <resource server name>
|
kanidm system oauth2 warning-insecure-client-disable-pkce <resource server name>
|
||||||
```
|
```
|
||||||
|
|
||||||
To enable legacy cryptograhy (RSA PKCS1-5 SHA256):
|
To enable legacy cryptograhy (RSA PKCS1-5 SHA256):
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
kanidm system oauth2 warning_enable_legacy_crypto <resource server name>
|
kanidm system oauth2 warning-enable-legacy-crypto <resource server name>
|
||||||
```
|
```
|
||||||
|
|
||||||
## Example Integrations
|
## Example Integrations
|
||||||
|
|
|
||||||
|
|
@ -66,8 +66,8 @@ For an account to use RADIUS they must first generate a RADIUS secret unique to
|
||||||
default, all accounts can self-create this secret.
|
default, all accounts can self-create this secret.
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
kanidm person radius generate_secret --name william william
|
kanidm person radius generate-secret --name william william
|
||||||
kanidm person radius show_secret --name william william
|
kanidm person radius show-secret --name william william
|
||||||
```
|
```
|
||||||
|
|
||||||
## Account Group Configuration
|
## Account Group Configuration
|
||||||
|
|
@ -97,7 +97,7 @@ kanidm group add_members --name admin idm_radius_servers radius_service_account
|
||||||
Now reset the account password, using the `admin` account:
|
Now reset the account password, using the `admin` account:
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
kanidm service-account credential generate-pw --name admin radius_service_account
|
kanidm service-account credential generate --name admin radius_service_account
|
||||||
```
|
```
|
||||||
|
|
||||||
## Deploying a RADIUS Container
|
## Deploying a RADIUS Container
|
||||||
|
|
|
||||||
|
|
@ -36,50 +36,7 @@ they require.
|
||||||
Kanidm acts as a central authority of accounts in your organisation and allows each account to
|
Kanidm acts as a central authority of accounts in your organisation and allows each account to
|
||||||
associate many devices and credentials with different privileges. An example of how this looks:
|
associate many devices and credentials with different privileges. An example of how this looks:
|
||||||
|
|
||||||
┌──────────────────┐
|
<img src="images/KanidmUseCases.png" alt="Kanidm Use Case Diagram" />
|
||||||
┌┴─────────────────┐│
|
|
||||||
│ ││
|
|
||||||
┌───────────────┬───▶│ Kanidm │◀─────┬─────────────────────────┐
|
|
||||||
│ │ │ ├┘ │ │
|
|
||||||
│ │ └──────────────────┘ │ Verify
|
|
||||||
Account Data │ ▲ │ Radius
|
|
||||||
References │ │ │ Password
|
|
||||||
│ │ │ │ │
|
|
||||||
│ │ │ │ ┌────────────┐
|
|
||||||
│ │ │ │ │ │
|
|
||||||
│ │ │ Verify │ RADIUS │
|
|
||||||
┌────────────┐ │ Retrieve SSH Application │ │
|
|
||||||
│ │ │ Public Keys Password └────────────┘
|
|
||||||
│ Database │ │ │ │ ▲
|
|
||||||
│ │ │ │ │ │
|
|
||||||
└────────────┘ │ │ │ ┌────────┴──────┐
|
|
||||||
▲ │ │ │ │ │
|
|
||||||
│ │ │ │ │ │
|
|
||||||
┌────────────┐ │ ┌────────────┐ ┌────────────┐ ┌────────────┐ ┌────────────┐
|
|
||||||
│ │ │ │ │ │ │ │ │ │ │
|
|
||||||
│ Web Site │ │ │ SSH │ │ Email │ │ WIFI │ │ VPN │
|
|
||||||
│ │ │ │ │ │ │ │ │ │ │
|
|
||||||
└────────────┘ │ └────────────┘ └────────────┘ └────────────┘ └────────────┘
|
|
||||||
▲ │ ▲ ▲ ▲ ▲
|
|
||||||
│ │ │ │ │ │
|
|
||||||
│ │ │ │ │ │
|
|
||||||
│ Login To │ │ │ │
|
|
||||||
SSO/Oauth Oauth/SSO SSH Keys Application Radius Radius
|
|
||||||
│ │ │ Password Password Password
|
|
||||||
│ │ │ │ │ │
|
|
||||||
│ │ │ │ │ │
|
|
||||||
│ │ │ │ │ │
|
|
||||||
│ │ ┌──────────┐ │ │ │
|
|
||||||
│ │ │ │ │ │ │
|
|
||||||
└──────────────┴────────│ Laptop │──────────┴───────────────┴───────────────┘
|
|
||||||
│ │
|
|
||||||
└──────────┘
|
|
||||||
▲
|
|
||||||
│
|
|
||||||
│
|
|
||||||
┌──────────┐
|
|
||||||
│ You │
|
|
||||||
└──────────┘
|
|
||||||
|
|
||||||
A key design goal is that you authenticate with your device in some manner, and then your device
|
A key design goal is that you authenticate with your device in some manner, and then your device
|
||||||
will continue to authenticate you in the future. Each of these different types of credentials, from
|
will continue to authenticate you in the future. Each of these different types of credentials, from
|
||||||
|
|
|
||||||
|
|
@ -4,28 +4,24 @@
|
||||||
|
|
||||||
> **NOTE** Our preferred deployment method is in containers, and this documentation assumes you're
|
> **NOTE** Our preferred deployment method is in containers, and this documentation assumes you're
|
||||||
> running in docker. Kanidm will alternately run as a daemon/service, and server builds are
|
> running in docker. Kanidm will alternately run as a daemon/service, and server builds are
|
||||||
> available for multiple platforms if you prefer this option.
|
> available for multiple platforms if you prefer this option. You will
|
||||||
|
|
||||||
We provide docker images for the server components. They can be found at:
|
We provide docker images for the server components. They can be found at:
|
||||||
|
|
||||||
- <https://hub.docker.com/r/kanidm/server>
|
- <https://hub.docker.com/r/kanidm/server>
|
||||||
- <https://hub.docker.com/r/kanidm/radius>
|
- <https://hub.docker.com/r/kanidm/radius>
|
||||||
|
- <https://hub.docker.com/r/kanidm/tools>
|
||||||
|
|
||||||
You can fetch these by running the commands:
|
You can fetch these by running the commands:
|
||||||
|
|
||||||
```bash
|
|
||||||
docker pull kanidm/server:x86_64_latest
|
|
||||||
docker pull kanidm/radius:latest
|
|
||||||
```
|
|
||||||
|
|
||||||
If you do not meet the [system requirements](#system-requirements) for your CPU you should use:
|
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
docker pull kanidm/server:latest
|
docker pull kanidm/server:latest
|
||||||
|
docker pull kanidm/radius:latest
|
||||||
|
docker pull kanidm/tools:latest
|
||||||
```
|
```
|
||||||
|
|
||||||
You may need to adjust your example commands throughout this document to suit your desired server
|
You may need to adjust your example commands throughout this document to suit your desired server
|
||||||
type.
|
type if you choose not to use docker.
|
||||||
|
|
||||||
## Development Version
|
## Development Version
|
||||||
|
|
||||||
|
|
@ -38,26 +34,14 @@ report issues, we will make every effort to help resolve them.
|
||||||
|
|
||||||
### CPU
|
### CPU
|
||||||
|
|
||||||
If you are using the x86\_64 cpu-optimised version, you must have a CPU that is from 2013 or newer
|
Kanidm relies on modern CPU optimisations for many operations. As a result your cpu must be either:
|
||||||
(Haswell, Ryzen). The following instruction flags are used.
|
|
||||||
|
|
||||||
```asm
|
- `x86_64` supporting `x86_64_v2` operations.
|
||||||
cmov, cx8, fxsr, mmx, sse, sse2, cx16, sahf, popcnt, sse3, sse4.1, sse4.2, avx, avx2,
|
- `aarch64` supporting `neon_v8` operations.
|
||||||
bmi, bmi2, f16c, fma, lzcnt, movbe, xsave
|
|
||||||
```
|
|
||||||
|
|
||||||
Older or unsupported CPUs may raise a SIGIL (Illegal Instruction) on hardware that is not supported
|
Older or unsupported CPUs may raise a SIGIL (Illegal Instruction) on hardware that is not supported
|
||||||
by the project.
|
by the project.
|
||||||
|
|
||||||
In this case, you should use the standard server:latest image.
|
|
||||||
|
|
||||||
In the future we may apply a baseline of flags as a requirement for x86\_64 for the server:latest
|
|
||||||
image. These flags will be:
|
|
||||||
|
|
||||||
```asm
|
|
||||||
cmov, cx8, fxsr, mmx, sse, sse2
|
|
||||||
```
|
|
||||||
|
|
||||||
<!-- deno-fmt-ignore-start -->
|
<!-- deno-fmt-ignore-start -->
|
||||||
|
|
||||||
{{#template templates/kani-alert.md
|
{{#template templates/kani-alert.md
|
||||||
|
|
@ -161,7 +145,8 @@ If these verifications pass you can now use these certificates with Kanidm. To p
|
||||||
in place you can use a shell container that mounts the volume such as:
|
in place you can use a shell container that mounts the volume such as:
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
docker run --rm -i -t -v kanidmd:/data -v /my/host/path/work:/work opensuse/leap:latest /bin/sh -c "cp /work/* /data/"
|
docker run --rm -i -t -v kanidmd:/data -v /my/host/path/work:/work opensuse/leap:latest \
|
||||||
|
/bin/sh -c "cp /work/* /data/"
|
||||||
```
|
```
|
||||||
|
|
||||||
OR for a shell into the volume:
|
OR for a shell into the volume:
|
||||||
|
|
|
||||||
|
|
@ -25,7 +25,7 @@ specification is required.
|
||||||
|
|
||||||
## How Long Do Items Stay in the Recycle Bin?
|
## How Long Do Items Stay in the Recycle Bin?
|
||||||
|
|
||||||
Currently they stay up to 1 week before they are removed.
|
Currently they stay up to 1 week before they are removed. This may change in the future though.
|
||||||
|
|
||||||
## Managing the Recycle Bin
|
## Managing the Recycle Bin
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -36,12 +36,24 @@ docker run --rm -i -t -v kanidmd:/data \
|
||||||
Then you can setup the initial admin account and initialise the database into your volume. This
|
Then you can setup the initial admin account and initialise the database into your volume. This
|
||||||
command will generate a new random password for the admin account.
|
command will generate a new random password for the admin account.
|
||||||
|
|
||||||
|
<!-- deno-fmt-ignore-start -->
|
||||||
|
|
||||||
|
{{#template templates/kani-warning.md
|
||||||
|
imagepath=images
|
||||||
|
title=Warning!
|
||||||
|
text=The server must not be running at this point, as it requires exclusive access to the database.
|
||||||
|
}}
|
||||||
|
|
||||||
|
<!-- deno-fmt-ignore-end -->
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
docker run --rm -i -t -v kanidmd:/data \
|
docker run --rm -i -t -v kanidmd:/data \
|
||||||
kanidm/server:latest /sbin/kanidmd recover_account -c /data/server.toml admin
|
kanidm/server:latest /sbin/kanidmd recover-account -c /data/server.toml admin
|
||||||
# success - recover_account password for user admin: vv...
|
# success - recovery of account password for admin: vv...
|
||||||
```
|
```
|
||||||
|
|
||||||
|
After the recovery is complete the server can be started again.
|
||||||
|
|
||||||
## Run the Server
|
## Run the Server
|
||||||
|
|
||||||
Now we can run the server so that it can accept connections. This defaults to using
|
Now we can run the server so that it can accept connections. This defaults to using
|
||||||
|
|
@ -61,3 +73,13 @@ docker to allow these port binds. You can add this with `--cap-add` in your dock
|
||||||
docker run --cap-add NET_BIND_SERVICE --network [host OR macvlan OR ipvlan] \
|
docker run --cap-add NET_BIND_SERVICE --network [host OR macvlan OR ipvlan] \
|
||||||
-v kanidmd:/data kanidm/server:latest
|
-v kanidmd:/data kanidm/server:latest
|
||||||
```
|
```
|
||||||
|
|
||||||
|
<!-- deno-fmt-ignore-start -->
|
||||||
|
|
||||||
|
{{#template templates/kani-alert.md
|
||||||
|
imagepath=images
|
||||||
|
title=Tip
|
||||||
|
text=However you choose to run your server, you should document and keep note of the docker run / create command you chose to start the instance. This will be used in the upgrade procedure.
|
||||||
|
}}
|
||||||
|
|
||||||
|
<!-- deno-fmt-ignore-end -->
|
||||||
|
|
|
||||||
|
|
@ -1,5 +1,19 @@
|
||||||
# Updating the Server
|
# Updating the Server
|
||||||
|
|
||||||
|
Docker doesn't follow a "traditional" method of updates. Rather you remove the old version of the
|
||||||
|
container and recreate it with a newer version. This document will help walk you through that
|
||||||
|
process.
|
||||||
|
|
||||||
|
<!-- deno-fmt-ignore-start -->
|
||||||
|
|
||||||
|
{{#template templates/kani-alert.md
|
||||||
|
imagepath=images
|
||||||
|
title=Tip
|
||||||
|
text=You should have documented and preserved your kanidm container create / run command from the server preparation guide. If not, you'll need to use "docker inspect" to work out how to recreate these parameters.
|
||||||
|
}}
|
||||||
|
|
||||||
|
<!-- deno-fmt-ignore-end -->
|
||||||
|
|
||||||
## Preserving the Previous Image
|
## Preserving the Previous Image
|
||||||
|
|
||||||
You may wish to preserve the previous image before updating. This is useful if an issue is
|
You may wish to preserve the previous image before updating. This is useful if an issue is
|
||||||
|
|
@ -12,11 +26,12 @@ docker tag kanidm/server:latest kanidm/server:2022-10-24
|
||||||
|
|
||||||
## Update your Image
|
## Update your Image
|
||||||
|
|
||||||
Pull the latest version of Kanidm that matches your CPU profile
|
Pull the latest version of Kanidm.
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
docker pull kanidm/server:latest
|
docker pull kanidm/server:latest
|
||||||
docker pull kanidm/server:x86_64_latest
|
docker pull kanidm/radius:latest
|
||||||
|
docker pull kanidm/tools:latest
|
||||||
```
|
```
|
||||||
|
|
||||||
## Perform a backup
|
## Perform a backup
|
||||||
|
|
@ -30,13 +45,13 @@ See [backup and restore](backup_restore.md)
|
||||||
{{#template templates/kani-warning.md
|
{{#template templates/kani-warning.md
|
||||||
imagepath=images
|
imagepath=images
|
||||||
title=WARNING
|
title=WARNING
|
||||||
text=It is not always guaranteed that downgrades are possible. It is critical you know how to backup and restore before you proceed with this step.
|
text=Downgrades are not possible. It is critical you know how to backup and restore before you proceed with this step.
|
||||||
}}
|
}}
|
||||||
|
|
||||||
<!-- deno-fmt-ignore-end -->
|
<!-- deno-fmt-ignore-end -->
|
||||||
|
|
||||||
Docker updates by deleting and recreating the instance. All that needs to be preserved in your
|
Docker updates by deleting and recreating the instance. All that needs to be preserved is contained
|
||||||
storage volume.
|
in your storage volume.
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
docker stop <previous instance name>
|
docker stop <previous instance name>
|
||||||
|
|
@ -49,10 +64,11 @@ docker run --rm -i -t -v kanidmd:/data \
|
||||||
kanidm/server:latest /sbin/kanidmd configtest -c /data/server.toml
|
kanidm/server:latest /sbin/kanidmd configtest -c /data/server.toml
|
||||||
```
|
```
|
||||||
|
|
||||||
You can then follow through with the upgrade
|
You can then follow through with the upgrade by running the create / run command with your existing
|
||||||
|
volume.
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
docker run -p PORTS -v kanidmd:/data \
|
docker run [Your Arguments Here] -v kanidmd:/data \
|
||||||
OTHER_CUSTOM_OPTIONS \
|
OTHER_CUSTOM_OPTIONS \
|
||||||
kanidm/server:latest
|
kanidm/server:latest
|
||||||
```
|
```
|
||||||
|
|
@ -76,5 +92,4 @@ If you deleted the previous instance, you can recreate it from your preserved ta
|
||||||
docker run -p ports -v volumes kanidm/server:<DATE>
|
docker run -p ports -v volumes kanidm/server:<DATE>
|
||||||
```
|
```
|
||||||
|
|
||||||
In some cases the downgrade to the previous instance may not work. If the server from your previous
|
If the server from your previous version fails to start, you will need to restore from backup.
|
||||||
version fails to start, you may need to restore from backup.
|
|
||||||
|
|
|
||||||
|
|
@ -9,21 +9,24 @@ on their accounts.
|
||||||
To view the current SSH public keys on accounts, you can use:
|
To view the current SSH public keys on accounts, you can use:
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
kanidm person|service-account ssh list_publickeys --name <login user> <account to view>
|
kanidm person|service-account \
|
||||||
kanidm person|service-account ssh list_publickeys --name idm_admin william
|
ssh list-publickeys --name <login user> <account to view>
|
||||||
|
kanidm person|service-account \
|
||||||
|
ssh list-publickeys --name idm_admin william
|
||||||
```
|
```
|
||||||
|
|
||||||
All users by default can self-manage their SSH public keys. To upload a key, a command like this is
|
All users by default can self-manage their SSH public keys. To upload a key, a command like this is
|
||||||
the best way to do so:
|
the best way to do so:
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
kanidm person|service-account ssh add_publickey --name william william 'test-key' "`cat ~/.ssh/id_rsa.pub`"
|
kanidm person|service-account \
|
||||||
|
ssh add-publickey --name william william 'test-key' "`cat ~/.ssh/id_ecdsa.pub`"
|
||||||
```
|
```
|
||||||
|
|
||||||
To remove (revoke) an SSH public key, delete them by the tag name:
|
To remove (revoke) an SSH public key, delete them by the tag name:
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
kanidm person|service-account ssh delete_publickey --name william william 'test-key'
|
kanidm person|service-account ssh delete-publickey --name william william 'test-key'
|
||||||
```
|
```
|
||||||
|
|
||||||
## Security Notes
|
## Security Notes
|
||||||
|
|
@ -32,7 +35,7 @@ As a security feature, Kanidm validates _all_ public keys to ensure they are val
|
||||||
Uploading a private key or other data will be rejected. For example:
|
Uploading a private key or other data will be rejected. For example:
|
||||||
|
|
||||||
```bash
|
```bash
|
||||||
kanidm person|service-account ssh add_publickey --name william william 'test-key' "invalid"
|
kanidm person|service-account ssh add-publickey --name william william 'test-key' "invalid"
|
||||||
Enter password:
|
Enter password:
|
||||||
... Some(SchemaViolation(InvalidAttributeSyntax)))' ...
|
... Some(SchemaViolation(InvalidAttributeSyntax)))' ...
|
||||||
```
|
```
|
||||||
|
|
@ -41,12 +44,12 @@ Enter password:
|
||||||
|
|
||||||
### Public Key Caching Configuration
|
### Public Key Caching Configuration
|
||||||
|
|
||||||
If you have kanidm_unixd running, you can use it to locally cache SSH public keys. This means you
|
If you have kanidm\_unixd running, you can use it to locally cache SSH public keys. This means you
|
||||||
can still SSH into your machines, even if your network is down, you move away from Kanidm, or some
|
can still SSH into your machines, even if your network is down, you move away from Kanidm, or some
|
||||||
other interruption occurs.
|
other interruption occurs.
|
||||||
|
|
||||||
The kanidm_ssh_authorizedkeys command is part of the kanidm-unix-clients package, so should be
|
The kanidm\_ssh\_authorizedkeys command is part of the kanidm-unix-clients package, so should be
|
||||||
installed on the servers. It communicates to kanidm_unixd, so you should have a configured
|
installed on the servers. It communicates to kanidm\_unixd, so you should have a configured
|
||||||
PAM/nsswitch setup as well.
|
PAM/nsswitch setup as well.
|
||||||
|
|
||||||
You can test this is configured correctly by running:
|
You can test this is configured correctly by running:
|
||||||
|
|
@ -73,7 +76,7 @@ It's highly recommended you keep your client configuration and sshd_configuratio
|
||||||
management tool such as salt or ansible.
|
management tool such as salt or ansible.
|
||||||
|
|
||||||
> **NOTICE:** With a working SSH key setup, you should also consider adding the following
|
> **NOTICE:** With a working SSH key setup, you should also consider adding the following
|
||||||
> sshd_config options as hardening.
|
> sshd\_config options as hardening.
|
||||||
|
|
||||||
```
|
```
|
||||||
PermitRootLogin no
|
PermitRootLogin no
|
||||||
|
|
@ -91,7 +94,7 @@ In this mode, the authorised keys commands will contact Kanidm directly.
|
||||||
> or communication loss may prevent you accessing your systems. You should only use this version if
|
> or communication loss may prevent you accessing your systems. You should only use this version if
|
||||||
> you have a requirement for it.
|
> you have a requirement for it.
|
||||||
|
|
||||||
The kanidm_ssh_authorizedkeys_direct command is part of the kanidm-clients package, so should be
|
The kanidm\_ssh\_authorizedkeys\_direct command is part of the kanidm-clients package, so should be
|
||||||
installed on the servers.
|
installed on the servers.
|
||||||
|
|
||||||
To configure the tool, you should edit /etc/kanidm/config, as documented in
|
To configure the tool, you should edit /etc/kanidm/config, as documented in
|
||||||
|
|
@ -105,8 +108,8 @@ kanidm_ssh_authorizedkeys_direct -D anonymous <account name>
|
||||||
|
|
||||||
If the account has SSH public keys you should see them listed, one per line.
|
If the account has SSH public keys you should see them listed, one per line.
|
||||||
|
|
||||||
To configure servers to accept these keys, you must change their /etc/ssh/sshd_config to contain the
|
To configure servers to accept these keys, you must change their /etc/ssh/sshd\_config to contain
|
||||||
lines:
|
the lines:
|
||||||
|
|
||||||
```
|
```
|
||||||
PubkeyAuthentication yes
|
PubkeyAuthentication yes
|
||||||
|
|
@ -117,5 +120,5 @@ AuthorizedKeysCommandUser nobody
|
||||||
|
|
||||||
Restart sshd, and then attempt to authenticate with the keys.
|
Restart sshd, and then attempt to authenticate with the keys.
|
||||||
|
|
||||||
It's highly recommended you keep your client configuration and sshd_configuration in a configuration
|
It's highly recommended you keep your client configuration and sshd\_configuration in a
|
||||||
management tool such as salt or ansible.
|
configuration management tool such as salt or ansible.
|
||||||
|
|
|
||||||
|
|
@ -58,7 +58,7 @@ You should ignore `cn=changelog` and `o=ipaca` as these are system internal nami
|
||||||
then create an ldapmodify like the following.
|
then create an ldapmodify like the following.
|
||||||
|
|
||||||
```rust
|
```rust
|
||||||
{{#rustdoc_include ../../../iam_migrations/freeipa/00config-mod.ldif}}
|
{{#rustdoc_include ../../../tools/iam_migrations/freeipa/00config-mod.ldif}}
|
||||||
```
|
```
|
||||||
|
|
||||||
And apply it with:
|
And apply it with:
|
||||||
|
|
|
||||||
|
|
@ -5,7 +5,7 @@ Some things to try.
|
||||||
## Is the server started?
|
## Is the server started?
|
||||||
|
|
||||||
If you don't see "ready to rock! 🪨" in your logs, it's not started. Scroll back and look for
|
If you don't see "ready to rock! 🪨" in your logs, it's not started. Scroll back and look for
|
||||||
errors!dd
|
errors!
|
||||||
|
|
||||||
## Can you connect?
|
## Can you connect?
|
||||||
|
|
||||||
|
|
@ -15,7 +15,7 @@ If the server's running on `idm.example.com:8443` then a simple connectivity tes
|
||||||
Run the following command:
|
Run the following command:
|
||||||
|
|
||||||
```shell
|
```shell
|
||||||
curl -k https://idm.example.com:8443/status
|
curl https://idm.example.com:8443/status
|
||||||
```
|
```
|
||||||
|
|
||||||
This is similar to what you _should_ see:
|
This is similar to what you _should_ see:
|
||||||
|
|
@ -48,7 +48,7 @@ If you get errors about certificates, try adding `-k` to skip certificate verifi
|
||||||
just test connectivity:
|
just test connectivity:
|
||||||
|
|
||||||
```
|
```
|
||||||
curl -vk https://idm.example.com:8443
|
curl -vk https://idm.example.com:8443/status
|
||||||
```
|
```
|
||||||
|
|
||||||
## Server things to check
|
## Server things to check
|
||||||
|
|
@ -56,9 +56,14 @@ curl -vk https://idm.example.com:8443
|
||||||
- Has the config file got `bindaddress = "127.0.0.1:8443"` ? Change it to
|
- Has the config file got `bindaddress = "127.0.0.1:8443"` ? Change it to
|
||||||
`bindaddress = "[::]:8443"`, so it listens on all interfaces.
|
`bindaddress = "[::]:8443"`, so it listens on all interfaces.
|
||||||
- Is there a firewall on the server?
|
- Is there a firewall on the server?
|
||||||
- If you're running in docker, did you expose the port? (`-p 8443:8443`)
|
- If you're running in docker, did you expose the port (`-p 8443:8443`) or configure the network to
|
||||||
|
host/macvlan/ipvlan?
|
||||||
|
|
||||||
## Client things to check
|
## Client errors
|
||||||
|
|
||||||
|
When you receive a client error it will list an "Operation ID" sometimes also called the OpId or
|
||||||
|
KOpId. This UUID matches to the UUID's in the logs allowing you to precisely locate the server logs
|
||||||
|
related to the failing operation.
|
||||||
|
|
||||||
Try running commands with `RUST_LOG=debug` to get more information:
|
Try running commands with `RUST_LOG=debug` to get more information:
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,5 +1,5 @@
|
||||||
# this should be at /etc/kanidm/unixd, and configures kanidm-unixd
|
# this should be at /etc/kanidm/unixd, and configures kanidm-unixd
|
||||||
# some documentation is here: https://github.com/kanidm/kanidm/blob/master/kanidm_book/src/pam_and_nsswitch.md
|
# some documentation is here: https://github.com/kanidm/kanidm/blob/master/book/src/pam_and_nsswitch.md
|
||||||
# pam_allowed_login_groups = ["posix_group"]
|
# pam_allowed_login_groups = ["posix_group"]
|
||||||
# default_shell = "/bin/sh"
|
# default_shell = "/bin/sh"
|
||||||
# home_prefix = "/home/"
|
# home_prefix = "/home/"
|
||||||
|
|
|
||||||
|
|
@ -2,7 +2,7 @@
|
||||||
db_path = "/tmp/kanidm-unixd"
|
db_path = "/tmp/kanidm-unixd"
|
||||||
sock_path = "/tmp/kanimd_unixd.sock"
|
sock_path = "/tmp/kanimd_unixd.sock"
|
||||||
task_sock_path = "/tmp/kanimd_unidx_task.sock"
|
task_sock_path = "/tmp/kanimd_unidx_task.sock"
|
||||||
# some documentation is here: https://github.com/kanidm/kanidm/blob/master/kanidm_book/src/pam_and_nsswitch.md
|
# some documentation is here: https://github.com/kanidm/kanidm/blob/master/book/src/pam_and_nsswitch.md
|
||||||
pam_allowed_login_groups = ["posix_group"]
|
pam_allowed_login_groups = ["posix_group"]
|
||||||
# default_shell = "/bin/sh"
|
# default_shell = "/bin/sh"
|
||||||
# home_prefix = "/home/"
|
# home_prefix = "/home/"
|
||||||
|
|
|
||||||
|
|
@ -38,7 +38,7 @@ pub fn readonly(meta: &Metadata) -> bool {
|
||||||
#[cfg(not(target_family = "unix"))]
|
#[cfg(not(target_family = "unix"))]
|
||||||
/// Check a given file's metadata is read-only for the current user (true = read-only) Stub function if you're building for windows!
|
/// Check a given file's metadata is read-only for the current user (true = read-only) Stub function if you're building for windows!
|
||||||
pub fn readonly(meta: &Metadata) -> bool {
|
pub fn readonly(meta: &Metadata) -> bool {
|
||||||
debug!(
|
eprintln!(
|
||||||
"Windows target asked to check metadata on {:?} returning false",
|
"Windows target asked to check metadata on {:?} returning false",
|
||||||
meta
|
meta
|
||||||
);
|
);
|
||||||
|
|
|
||||||
|
|
@ -1,3 +0,0 @@
|
||||||
web_ui_pkg_path = "/pkg"
|
|
||||||
# Define this to override the arch.
|
|
||||||
cpu_flags = "x86_64_v3"
|
|
||||||
|
|
@ -10,9 +10,9 @@ if [ "$(uname -m)" = "aarch64" ] && [ "$(uname -s)" = "Linux" ]; then
|
||||||
echo " Large WASM ahead."
|
echo " Large WASM ahead."
|
||||||
echo "#####################################"
|
echo "#####################################"
|
||||||
|
|
||||||
if [ "$(grep -oE 'wasm-opt.*' kanidmd_web_ui/Cargo.toml | awk '{print $NF}')" != "false" ]; then
|
if [ "$(grep -oE 'wasm-opt.*' server/web_ui/Cargo.toml | awk '{print $NF}')" != "false" ]; then
|
||||||
echo "Updating kanidmd_web_ui/Cargo.toml to disable wasm-opt"
|
echo "Updating server/web_ui/Cargo.toml to disable wasm-opt"
|
||||||
cat >> kanidmd_web_ui/Cargo.toml <<-EOM
|
cat >> server/web_ui/Cargo.toml <<-EOM
|
||||||
[package.metadata.wasm-pack.profile.release]
|
[package.metadata.wasm-pack.profile.release]
|
||||||
wasm-opt = false
|
wasm-opt = false
|
||||||
EOM
|
EOM
|
||||||
|
|
|
||||||
|
|
@ -30,7 +30,7 @@ override_dh_auto_build:
|
||||||
KANIDM_BUILD_PROFILE=release_suse_generic dh_auto_build -- release/${PACKAGE}
|
KANIDM_BUILD_PROFILE=release_suse_generic dh_auto_build -- release/${PACKAGE}
|
||||||
./platform/debian/fix_wasm_opt.sh
|
./platform/debian/fix_wasm_opt.sh
|
||||||
cargo install wasm-pack --force
|
cargo install wasm-pack --force
|
||||||
cd kanidmd_web_ui && ./build_wasm.sh
|
cd server/web_ui && ./build_wasm.sh
|
||||||
|
|
||||||
override_dh_auto_test:
|
override_dh_auto_test:
|
||||||
override_dh_shlibdeps:
|
override_dh_shlibdeps:
|
||||||
|
|
@ -56,7 +56,7 @@ override_dh_auto_install:
|
||||||
target/release/kanidmd \
|
target/release/kanidmd \
|
||||||
${BINDIR}
|
${BINDIR}
|
||||||
mkdir -p ${PKGDIR}/usr/share/kanidm/ui/
|
mkdir -p ${PKGDIR}/usr/share/kanidm/ui/
|
||||||
cp -R kanidmd_web_ui/pkg ${PKGDIR}/usr/share/kanidm/ui/
|
cp -R server/web_ui/pkg ${PKGDIR}/usr/share/kanidm/ui/
|
||||||
|
|
||||||
override_dh_installexamples:
|
override_dh_installexamples:
|
||||||
mkdir -p ${SHARED_DIR}
|
mkdir -p ${SHARED_DIR}
|
||||||
|
|
|
||||||
|
|
@ -154,7 +154,7 @@ impl fmt::Display for AccountChangeMessage {
|
||||||
),
|
),
|
||||||
ConsoleOutputMode::Text => write!(
|
ConsoleOutputMode::Text => write!(
|
||||||
f,
|
f,
|
||||||
"{} - {} for user {}: {}",
|
"{} - {} for {}: {}",
|
||||||
self.status, self.action, self.dest_user, self.result,
|
self.status, self.action, self.dest_user, self.result,
|
||||||
),
|
),
|
||||||
}
|
}
|
||||||
|
|
|
||||||
|
|
@ -29,8 +29,8 @@ RUN \
|
||||||
openssl \
|
openssl \
|
||||||
curl
|
curl
|
||||||
|
|
||||||
ADD kanidm_rlm_python/mods-available/ /etc/raddb/mods-available/
|
ADD rlm_python/mods-available/ /etc/raddb/mods-available/
|
||||||
COPY kanidm_rlm_python/sites-available/ /etc/raddb/sites-available/
|
COPY rlm_python/sites-available/ /etc/raddb/sites-available/
|
||||||
|
|
||||||
# Set a working directory of /etc/raddb
|
# Set a working directory of /etc/raddb
|
||||||
WORKDIR /etc/raddb
|
WORKDIR /etc/raddb
|
||||||
|
|
@ -55,7 +55,7 @@ COPY pykanidm/ /pkg/pykanidm/
|
||||||
RUN python3 -m pip install --no-cache-dir --no-warn-script-location /pkg/pykanidm && \
|
RUN python3 -m pip install --no-cache-dir --no-warn-script-location /pkg/pykanidm && \
|
||||||
rm -rf /pkg/*
|
rm -rf /pkg/*
|
||||||
|
|
||||||
COPY kanidm_rlm_python/radius_entrypoint.py /radius_entrypoint.py
|
COPY rlm_python/radius_entrypoint.py /radius_entrypoint.py
|
||||||
|
|
||||||
ENV LD_PRELOAD=/usr/lib64/libpython3.so
|
ENV LD_PRELOAD=/usr/lib64/libpython3.so
|
||||||
ENV KANIDM_CONFIG_FILE="/data/kanidm"
|
ENV KANIDM_CONFIG_FILE="/data/kanidm"
|
||||||
|
|
|
||||||
|
|
@ -25,11 +25,11 @@ function build_version() {
|
||||||
git switch -c "${BOOK_VERSION}" || git switch "${BOOK_VERSION}"
|
git switch -c "${BOOK_VERSION}" || git switch "${BOOK_VERSION}"
|
||||||
fi
|
fi
|
||||||
echo "Running mdbook build"
|
echo "Running mdbook build"
|
||||||
mdbook build kanidm_book
|
mdbook build book
|
||||||
echo "Running cargo doc"
|
echo "Running cargo doc"
|
||||||
cargo doc --quiet --no-deps
|
cargo doc --quiet --no-deps
|
||||||
echo "Moving book to ${DOCS_DIR}/${BOOK_VERSION}/"
|
echo "Moving book to ${DOCS_DIR}/${BOOK_VERSION}/"
|
||||||
mv ./kanidm_book/book/ "${DOCS_DIR}/${BOOK_VERSION}/"
|
mv ./book/book/ "${DOCS_DIR}/${BOOK_VERSION}/"
|
||||||
echo "Cleaning out rustdoc dir..."
|
echo "Cleaning out rustdoc dir..."
|
||||||
rm -rf "${DOCS_DIR}/${BOOK_VERSION}/rustdoc/"
|
rm -rf "${DOCS_DIR}/${BOOK_VERSION}/rustdoc/"
|
||||||
echo "Moving rustdoc to ${DOCS_DIR}/${BOOK_VERSION}/rustdoc/"
|
echo "Moving rustdoc to ${DOCS_DIR}/${BOOK_VERSION}/rustdoc/"
|
||||||
|
|
|
||||||
|
|
@ -35,7 +35,7 @@ COPY . /usr/src/kanidm
|
||||||
|
|
||||||
# ======================
|
# ======================
|
||||||
|
|
||||||
# WORKDIR /usr/src/kanidm/kanidmd_web_ui
|
# WORKDIR /usr/src/kanidm/server/web_ui
|
||||||
# # This can't be used in the wasm build for now.
|
# # This can't be used in the wasm build for now.
|
||||||
# # ENV RUSTFLAGS="-Clinker=clang"
|
# # ENV RUSTFLAGS="-Clinker=clang"
|
||||||
# RUN ./build_wasm.sh
|
# RUN ./build_wasm.sh
|
||||||
|
|
@ -71,7 +71,7 @@ RUN \
|
||||||
pam
|
pam
|
||||||
|
|
||||||
COPY --from=builder /usr/src/kanidm/target/release/kanidmd /sbin/
|
COPY --from=builder /usr/src/kanidm/target/release/kanidmd /sbin/
|
||||||
COPY --from=builder /usr/src/kanidm/kanidmd_web_ui/pkg /pkg
|
COPY --from=builder /usr/src/kanidm/server/web_ui/pkg /pkg
|
||||||
RUN chmod +x /sbin/kanidmd
|
RUN chmod +x /sbin/kanidmd
|
||||||
|
|
||||||
EXPOSE 8443 3636
|
EXPOSE 8443 3636
|
||||||
|
|
|
||||||
|
|
@ -195,7 +195,8 @@ impl<State: Clone + Send + Sync + 'static> tide::Middleware<State>
|
||||||
"worker-src 'none'",
|
"worker-src 'none'",
|
||||||
// TODO: Content-Security-Policy-Report-Only https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Content-Security-Policy-Report-Only
|
// TODO: Content-Security-Policy-Report-Only https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Content-Security-Policy-Report-Only
|
||||||
// "report-to 'none'", // unsupported by a lot of things still, but mozilla's saying report-uri is deprecated?
|
// "report-to 'none'", // unsupported by a lot of things still, but mozilla's saying report-uri is deprecated?
|
||||||
"report-uri 'none'",
|
// Commented because when violated this attempts to post to "'none'" as a url
|
||||||
|
// "report-uri 'none'",
|
||||||
"base-uri 'self'",
|
"base-uri 'self'",
|
||||||
// nobody wants to be in a frame
|
// nobody wants to be in a frame
|
||||||
"frame-ancestors 'none'",
|
"frame-ancestors 'none'",
|
||||||
|
|
|
||||||
|
|
@ -548,7 +548,7 @@ pub async fn recover_account_core(config: &Configuration, name: &str) {
|
||||||
src_user: String::from("command-line invocation"),
|
src_user: String::from("command-line invocation"),
|
||||||
dest_user: name.to_string(),
|
dest_user: name.to_string(),
|
||||||
result: new_pw,
|
result: new_pw,
|
||||||
action: String::from("recover_account password"),
|
action: String::from("recovery of account password"),
|
||||||
}
|
}
|
||||||
);
|
);
|
||||||
}
|
}
|
||||||
|
|
|
||||||
|
|
@ -217,6 +217,7 @@ async fn main() {
|
||||||
if kanidm_lib_file_permissions::readonly(&i_meta) {
|
if kanidm_lib_file_permissions::readonly(&i_meta) {
|
||||||
eprintln!("WARNING: DB folder permissions on {} indicate it may not be RW. This could cause the server start up to fail!", db_par_path_buf.to_str().unwrap_or("invalid file path"));
|
eprintln!("WARNING: DB folder permissions on {} indicate it may not be RW. This could cause the server start up to fail!", db_par_path_buf.to_str().unwrap_or("invalid file path"));
|
||||||
}
|
}
|
||||||
|
#[cfg(not(target_os="windows"))]
|
||||||
if i_meta.mode() & 0o007 != 0 {
|
if i_meta.mode() & 0o007 != 0 {
|
||||||
eprintln!("WARNING: DB folder {} has 'everyone' permission bits in the mode. This could be a security risk ...", db_par_path_buf.to_str().unwrap_or("invalid file path"));
|
eprintln!("WARNING: DB folder {} has 'everyone' permission bits in the mode. This could be a security risk ...", db_par_path_buf.to_str().unwrap_or("invalid file path"));
|
||||||
}
|
}
|
||||||
|
|
@ -266,6 +267,7 @@ async fn main() {
|
||||||
if !kanidm_lib_file_permissions::readonly(&i_meta) {
|
if !kanidm_lib_file_permissions::readonly(&i_meta) {
|
||||||
eprintln!("WARNING: permissions on {} may not be secure. Should be readonly to running uid. This could be a security risk ...", i_str);
|
eprintln!("WARNING: permissions on {} may not be secure. Should be readonly to running uid. This could be a security risk ...", i_str);
|
||||||
}
|
}
|
||||||
|
#[cfg(not(target_os="windows"))]
|
||||||
if i_meta.mode() & 0o007 != 0 {
|
if i_meta.mode() & 0o007 != 0 {
|
||||||
eprintln!("WARNING: {} has 'everyone' permission bits in the mode. This could be a security risk ...", i_str);
|
eprintln!("WARNING: {} has 'everyone' permission bits in the mode. This could be a security risk ...", i_str);
|
||||||
}
|
}
|
||||||
|
|
|
||||||
|
|
@ -102,22 +102,22 @@ struct DbScanGetId2Entry {
|
||||||
|
|
||||||
#[derive(Debug, Subcommand)]
|
#[derive(Debug, Subcommand)]
|
||||||
enum DbScanOpt {
|
enum DbScanOpt {
|
||||||
#[clap(name = "list_all_indexes")]
|
#[clap(name = "list-all-indexes")]
|
||||||
/// List all index tables that exist on the system.
|
/// List all index tables that exist on the system.
|
||||||
ListIndexes(CommonOpt),
|
ListIndexes(CommonOpt),
|
||||||
#[clap(name = "list_index")]
|
#[clap(name = "list-index")]
|
||||||
/// List all content of a named index
|
/// List all content of a named index
|
||||||
ListIndex(DbScanListIndex),
|
ListIndex(DbScanListIndex),
|
||||||
// #[structopt(name = "get_index")]
|
// #[structopt(name = "get_index")]
|
||||||
// /// Display the content of a single index key
|
// /// Display the content of a single index key
|
||||||
// GetIndex(DbScanGetIndex),
|
// GetIndex(DbScanGetIndex),
|
||||||
#[clap(name = "list_id2entry")]
|
#[clap(name = "list-id2entry")]
|
||||||
/// List all id2entry values with reduced entry content
|
/// List all id2entry values with reduced entry content
|
||||||
ListId2Entry(CommonOpt),
|
ListId2Entry(CommonOpt),
|
||||||
#[clap(name = "get_id2entry")]
|
#[clap(name = "get-id2entry")]
|
||||||
/// View the data of a specific entry from id2entry
|
/// View the data of a specific entry from id2entry
|
||||||
GetId2Entry(DbScanGetId2Entry),
|
GetId2Entry(DbScanGetId2Entry),
|
||||||
#[clap(name = "list_index_analysis")]
|
#[clap(name = "list-index-analysis")]
|
||||||
/// List all content of index analysis
|
/// List all content of index analysis
|
||||||
ListIndexAnalysis(CommonOpt),
|
ListIndexAnalysis(CommonOpt),
|
||||||
}
|
}
|
||||||
|
|
@ -136,12 +136,12 @@ enum KanidmdOpt {
|
||||||
#[clap(name = "configtest")]
|
#[clap(name = "configtest")]
|
||||||
/// Test the IDM Server configuration, without starting network listeners.
|
/// Test the IDM Server configuration, without starting network listeners.
|
||||||
ConfigTest(CommonOpt),
|
ConfigTest(CommonOpt),
|
||||||
#[clap(name = "recover_account")]
|
#[clap(name = "recover-account")]
|
||||||
/// Recover an account's password
|
/// Recover an account's password
|
||||||
RecoverAccount(RecoverAccountOpt),
|
RecoverAccount(RecoverAccountOpt),
|
||||||
// #[clap(name = "reset_server_id")]
|
// #[clap(name = "reset_server_id")]
|
||||||
// ResetServerId(CommonOpt),
|
// ResetServerId(CommonOpt),
|
||||||
#[clap(name = "db_scan")]
|
#[clap(name = "db-scan")]
|
||||||
/// Inspect the internal content of the database datastructures.
|
/// Inspect the internal content of the database datastructures.
|
||||||
DbScan {
|
DbScan {
|
||||||
#[clap(subcommand)]
|
#[clap(subcommand)]
|
||||||
|
|
|
||||||
|
|
@ -3,7 +3,7 @@
|
||||||
# This builds the assets for the Web UI, defaulting to a release build.
|
# This builds the assets for the Web UI, defaulting to a release build.
|
||||||
|
|
||||||
if [ ! -f build_wasm.sh ]; then
|
if [ ! -f build_wasm.sh ]; then
|
||||||
echo "Please run from the crate directory. (kanidmd_web_ui)"
|
echo "Please run from the crate directory. (server/web_ui)"
|
||||||
exit 1
|
exit 1
|
||||||
fi
|
fi
|
||||||
|
|
||||||
|
|
@ -28,8 +28,8 @@ wasm-pack build ${BUILD_FLAGS} --target web || exit 1
|
||||||
touch ./pkg/ANYTHING_HERE_WILL_BE_DELETED_ADD_TO_SRC && \
|
touch ./pkg/ANYTHING_HERE_WILL_BE_DELETED_ADD_TO_SRC && \
|
||||||
rsync --delete-after -r --copy-links -v ./src/img/ ./pkg/img/ && \
|
rsync --delete-after -r --copy-links -v ./src/img/ ./pkg/img/ && \
|
||||||
rsync --delete-after -r --copy-links -v ./src/external/ ./pkg/external/ && \
|
rsync --delete-after -r --copy-links -v ./src/external/ ./pkg/external/ && \
|
||||||
cp ../README.md ./pkg/
|
cp ../../README.md ./pkg/
|
||||||
cp ../LICENSE.md ./pkg/
|
cp ../../LICENSE.md ./pkg/
|
||||||
cp ./src/style.css ./pkg/style.css && \
|
cp ./src/style.css ./pkg/style.css && \
|
||||||
cp ./src/wasmloader.js ./pkg/wasmloader.js && \
|
cp ./src/wasmloader.js ./pkg/wasmloader.js && \
|
||||||
rm ./pkg/.gitignore
|
rm ./pkg/.gitignore
|
||||||
|
|
|
||||||
|
|
@ -52,7 +52,7 @@ See our [code of conduct]
|
||||||
See our documentation on [rights and ethics]
|
See our documentation on [rights and ethics]
|
||||||
|
|
||||||
[code of conduct]: https://github.com/kanidm/kanidm/blob/master/CODE_OF_CONDUCT.md
|
[code of conduct]: https://github.com/kanidm/kanidm/blob/master/CODE_OF_CONDUCT.md
|
||||||
[rights and ethics]: https://github.com/kanidm/kanidm/blob/master/ethics/README.md
|
[rights and ethics]: https://github.com/kanidm/kanidm/blob/master/project_docs/ethics/README.md
|
||||||
|
|
||||||
## Getting in Contact / Questions
|
## Getting in Contact / Questions
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -233,19 +233,19 @@ function addBorrowedObject(obj) {
|
||||||
}
|
}
|
||||||
function __wbg_adapter_48(arg0, arg1, arg2) {
|
function __wbg_adapter_48(arg0, arg1, arg2) {
|
||||||
try {
|
try {
|
||||||
wasm._dyn_core__ops__function__FnMut___A____Output___R_as_wasm_bindgen__closure__WasmClosure___describe__invoke__hd2dc42f7ea9500e6(arg0, arg1, addBorrowedObject(arg2));
|
wasm._dyn_core__ops__function__FnMut___A____Output___R_as_wasm_bindgen__closure__WasmClosure___describe__invoke__h1a2425c1ff443c06(arg0, arg1, addBorrowedObject(arg2));
|
||||||
} finally {
|
} finally {
|
||||||
heap[stack_pointer++] = undefined;
|
heap[stack_pointer++] = undefined;
|
||||||
}
|
}
|
||||||
}
|
}
|
||||||
|
|
||||||
function __wbg_adapter_51(arg0, arg1, arg2) {
|
function __wbg_adapter_51(arg0, arg1, arg2) {
|
||||||
wasm._dyn_core__ops__function__FnMut__A____Output___R_as_wasm_bindgen__closure__WasmClosure___describe__invoke__h24986de976067b9f(arg0, arg1, addHeapObject(arg2));
|
wasm._dyn_core__ops__function__FnMut__A____Output___R_as_wasm_bindgen__closure__WasmClosure___describe__invoke__h67535681ec7e0a05(arg0, arg1, addHeapObject(arg2));
|
||||||
}
|
}
|
||||||
|
|
||||||
function __wbg_adapter_54(arg0, arg1, arg2) {
|
function __wbg_adapter_54(arg0, arg1, arg2) {
|
||||||
try {
|
try {
|
||||||
wasm._dyn_core__ops__function__FnMut___A____Output___R_as_wasm_bindgen__closure__WasmClosure___describe__invoke__hf526198f1b682d58(arg0, arg1, addBorrowedObject(arg2));
|
wasm._dyn_core__ops__function__FnMut___A____Output___R_as_wasm_bindgen__closure__WasmClosure___describe__invoke__h5a26dea6ead0b9dc(arg0, arg1, addBorrowedObject(arg2));
|
||||||
} finally {
|
} finally {
|
||||||
heap[stack_pointer++] = undefined;
|
heap[stack_pointer++] = undefined;
|
||||||
}
|
}
|
||||||
|
|
@ -1148,15 +1148,15 @@ function getImports() {
|
||||||
const ret = wasm.memory;
|
const ret = wasm.memory;
|
||||||
return addHeapObject(ret);
|
return addHeapObject(ret);
|
||||||
};
|
};
|
||||||
imports.wbg.__wbindgen_closure_wrapper4728 = function(arg0, arg1, arg2) {
|
imports.wbg.__wbindgen_closure_wrapper4729 = function(arg0, arg1, arg2) {
|
||||||
const ret = makeMutClosure(arg0, arg1, 1095, __wbg_adapter_48);
|
const ret = makeMutClosure(arg0, arg1, 1095, __wbg_adapter_48);
|
||||||
return addHeapObject(ret);
|
return addHeapObject(ret);
|
||||||
};
|
};
|
||||||
imports.wbg.__wbindgen_closure_wrapper5583 = function(arg0, arg1, arg2) {
|
imports.wbg.__wbindgen_closure_wrapper5585 = function(arg0, arg1, arg2) {
|
||||||
const ret = makeMutClosure(arg0, arg1, 1426, __wbg_adapter_51);
|
const ret = makeMutClosure(arg0, arg1, 1426, __wbg_adapter_51);
|
||||||
return addHeapObject(ret);
|
return addHeapObject(ret);
|
||||||
};
|
};
|
||||||
imports.wbg.__wbindgen_closure_wrapper5661 = function(arg0, arg1, arg2) {
|
imports.wbg.__wbindgen_closure_wrapper5663 = function(arg0, arg1, arg2) {
|
||||||
const ret = makeMutClosure(arg0, arg1, 1456, __wbg_adapter_54);
|
const ret = makeMutClosure(arg0, arg1, 1456, __wbg_adapter_54);
|
||||||
return addHeapObject(ret);
|
return addHeapObject(ret);
|
||||||
};
|
};
|
||||||
|
|
|
||||||
Binary file not shown.
|
|
@ -106,7 +106,7 @@ pub async fn get_accounts() -> Result<AdminListAccountsMsg, GetError> {
|
||||||
let data: Vec<Entity> = match response.json().await {
|
let data: Vec<Entity> = match response.json().await {
|
||||||
Ok(value) => value,
|
Ok(value) => value,
|
||||||
|
|
||||||
// TODO: this kind of thing comes back when you're logged out: SerdeError(Error("invalid type: string \"sessionexpired\", expected a sequence", line: 1, column: 16))', kanidmd_web_ui/src/components/admin_accounts.rs:107:27
|
// TODO: this kind of thing comes back when you're logged out: SerdeError(Error("invalid type: string \"sessionexpired\", expected a sequence", line: 1, column: 16))', server/web_ui/src/components/admin_accounts.rs:107:27
|
||||||
Err(error) => {
|
Err(error) => {
|
||||||
return Err(GetError {
|
return Err(GetError {
|
||||||
err: format!("Failed to grab the account data into JSON: {:?}", error),
|
err: format!("Failed to grab the account data into JSON: {:?}", error),
|
||||||
|
|
|
||||||
|
|
@ -72,20 +72,20 @@ pub enum GroupOpt {
|
||||||
#[clap(name = "delete")]
|
#[clap(name = "delete")]
|
||||||
Delete(Named),
|
Delete(Named),
|
||||||
/// List the members of a group
|
/// List the members of a group
|
||||||
#[clap(name = "list_members")]
|
#[clap(name = "list-members")]
|
||||||
ListMembers(Named),
|
ListMembers(Named),
|
||||||
/// Set the exact list of members that this group should contain, removing any not listed in the
|
/// Set the exact list of members that this group should contain, removing any not listed in the
|
||||||
/// set operation.
|
/// set operation.
|
||||||
#[clap(name = "set_members")]
|
#[clap(name = "set-members")]
|
||||||
SetMembers(GroupNamedMembers),
|
SetMembers(GroupNamedMembers),
|
||||||
/// Delete all members of a group.
|
/// Delete all members of a group.
|
||||||
#[clap(name = "purge_members")]
|
#[clap(name = "purge-members")]
|
||||||
PurgeMembers(Named),
|
PurgeMembers(Named),
|
||||||
/// Add new members to a group
|
/// Add new members to a group
|
||||||
#[clap(name = "add_members")]
|
#[clap(name = "add-members")]
|
||||||
AddMembers(GroupNamedMembers),
|
AddMembers(GroupNamedMembers),
|
||||||
/// Remove the named members from this group
|
/// Remove the named members from this group
|
||||||
#[clap(name = "remove_members")]
|
#[clap(name = "remove-members")]
|
||||||
RemoveMembers(GroupNamedMembers),
|
RemoveMembers(GroupNamedMembers),
|
||||||
/// Manage posix extensions for this group allowing groups to be used on unix/linux systems
|
/// Manage posix extensions for this group allowing groups to be used on unix/linux systems
|
||||||
#[clap(name = "posix")]
|
#[clap(name = "posix")]
|
||||||
|
|
@ -168,7 +168,7 @@ pub struct UseResetTokenOpt {
|
||||||
pub struct AccountCreateOpt {
|
pub struct AccountCreateOpt {
|
||||||
#[clap(flatten)]
|
#[clap(flatten)]
|
||||||
aopts: AccountCommonOpt,
|
aopts: AccountCommonOpt,
|
||||||
#[clap(name = "display_name")]
|
#[clap(name = "display-name")]
|
||||||
display_name: String,
|
display_name: String,
|
||||||
#[clap(flatten)]
|
#[clap(flatten)]
|
||||||
copt: CommonOpt,
|
copt: CommonOpt,
|
||||||
|
|
@ -183,11 +183,11 @@ pub enum AccountCredential {
|
||||||
#[clap(name = "update")]
|
#[clap(name = "update")]
|
||||||
Update(AccountNamedOpt),
|
Update(AccountNamedOpt),
|
||||||
/// Using a reset token, interactively reset credentials for a user
|
/// Using a reset token, interactively reset credentials for a user
|
||||||
#[clap(name = "use_reset_token")]
|
#[clap(name = "use-reset-token")]
|
||||||
UseResetToken(UseResetTokenOpt),
|
UseResetToken(UseResetTokenOpt),
|
||||||
/// Create a reset token that can be given to another person so they can
|
/// Create a reset token that can be given to another person so they can
|
||||||
/// recover or reset their account credentials.
|
/// recover or reset their account credentials.
|
||||||
#[clap(name = "create_reset_token")]
|
#[clap(name = "create-reset-token")]
|
||||||
CreateResetToken(AccountNamedOpt),
|
CreateResetToken(AccountNamedOpt),
|
||||||
}
|
}
|
||||||
|
|
||||||
|
|
@ -195,12 +195,12 @@ pub enum AccountCredential {
|
||||||
#[derive(Debug, Subcommand)]
|
#[derive(Debug, Subcommand)]
|
||||||
pub enum AccountRadius {
|
pub enum AccountRadius {
|
||||||
/// Show the RADIUS secret for a user.
|
/// Show the RADIUS secret for a user.
|
||||||
#[clap(name = "show_secret")]
|
#[clap(name = "show-secret")]
|
||||||
Show(AccountNamedOpt),
|
Show(AccountNamedOpt),
|
||||||
/// Generate a randomized RADIUS secret for a user.
|
/// Generate a randomized RADIUS secret for a user.
|
||||||
#[clap(name = "generate_secret")]
|
#[clap(name = "generate-secret")]
|
||||||
Generate(AccountNamedOpt),
|
Generate(AccountNamedOpt),
|
||||||
#[clap(name = "delete_secret")]
|
#[clap(name = "delete-secret")]
|
||||||
/// Remove the configured RADIUS secret for the user.
|
/// Remove the configured RADIUS secret for the user.
|
||||||
DeleteSecret(AccountNamedOpt),
|
DeleteSecret(AccountNamedOpt),
|
||||||
}
|
}
|
||||||
|
|
@ -223,7 +223,7 @@ pub enum PersonPosix {
|
||||||
Show(AccountNamedOpt),
|
Show(AccountNamedOpt),
|
||||||
#[clap(name = "set")]
|
#[clap(name = "set")]
|
||||||
Set(AccountPosixOpt),
|
Set(AccountPosixOpt),
|
||||||
#[clap(name = "set_password")]
|
#[clap(name = "set-password")]
|
||||||
SetPassword(AccountNamedOpt),
|
SetPassword(AccountNamedOpt),
|
||||||
}
|
}
|
||||||
|
|
||||||
|
|
@ -257,11 +257,11 @@ pub struct PersonUpdateOpt {
|
||||||
|
|
||||||
#[derive(Debug, Subcommand)]
|
#[derive(Debug, Subcommand)]
|
||||||
pub enum AccountSsh {
|
pub enum AccountSsh {
|
||||||
#[clap(name = "list_publickeys")]
|
#[clap(name = "list-publickeys")]
|
||||||
List(AccountNamedOpt),
|
List(AccountNamedOpt),
|
||||||
#[clap(name = "add_publickey")]
|
#[clap(name = "add-publickey")]
|
||||||
Add(AccountNamedTagPkOpt),
|
Add(AccountNamedTagPkOpt),
|
||||||
#[clap(name = "delete_publickey")]
|
#[clap(name = "delete-publickey")]
|
||||||
Delete(AccountNamedTagOpt),
|
Delete(AccountNamedTagOpt),
|
||||||
}
|
}
|
||||||
|
|
||||||
|
|
@ -271,10 +271,10 @@ pub enum AccountValidity {
|
||||||
#[clap(name = "show")]
|
#[clap(name = "show")]
|
||||||
Show(AccountNamedOpt),
|
Show(AccountNamedOpt),
|
||||||
/// Set an accounts expiry time
|
/// Set an accounts expiry time
|
||||||
#[clap(name = "expire_at")]
|
#[clap(name = "expire-at")]
|
||||||
ExpireAt(AccountNamedExpireDateTimeOpt),
|
ExpireAt(AccountNamedExpireDateTimeOpt),
|
||||||
/// Set an account valid from time
|
/// Set an account valid from time
|
||||||
#[clap(name = "begin_from")]
|
#[clap(name = "begin-from")]
|
||||||
BeginFrom(AccountNamedValidDateTimeOpt),
|
BeginFrom(AccountNamedValidDateTimeOpt),
|
||||||
}
|
}
|
||||||
|
|
||||||
|
|
@ -292,7 +292,7 @@ pub enum AccountUserAuthToken {
|
||||||
#[clap(flatten)]
|
#[clap(flatten)]
|
||||||
copt: CommonOpt,
|
copt: CommonOpt,
|
||||||
/// The UUID of the token to destroy.
|
/// The UUID of the token to destroy.
|
||||||
#[clap(name = "session_id")]
|
#[clap(name = "session-id")]
|
||||||
session_id: Uuid,
|
session_id: Uuid,
|
||||||
},
|
},
|
||||||
}
|
}
|
||||||
|
|
@ -395,7 +395,7 @@ pub enum ServiceAccountApiToken {
|
||||||
#[clap(flatten)]
|
#[clap(flatten)]
|
||||||
copt: CommonOpt,
|
copt: CommonOpt,
|
||||||
/// The UUID of the token to destroy.
|
/// The UUID of the token to destroy.
|
||||||
#[clap(name = "token_id")]
|
#[clap(name = "token-id")]
|
||||||
token_id: Uuid,
|
token_id: Uuid,
|
||||||
},
|
},
|
||||||
}
|
}
|
||||||
|
|
@ -627,7 +627,7 @@ pub enum Oauth2Opt {
|
||||||
#[clap(name = "update-scope-map", visible_aliases=&["create-scope-map"])]
|
#[clap(name = "update-scope-map", visible_aliases=&["create-scope-map"])]
|
||||||
/// Update or add a new mapping from a group to scopes that it provides to members
|
/// Update or add a new mapping from a group to scopes that it provides to members
|
||||||
UpdateScopeMap(Oauth2CreateScopeMapOpt),
|
UpdateScopeMap(Oauth2CreateScopeMapOpt),
|
||||||
#[clap(name = "delete_scope_map")]
|
#[clap(name = "delete-scope-map")]
|
||||||
/// Remove a mapping from groups to scopes
|
/// Remove a mapping from groups to scopes
|
||||||
DeleteScopeMap(Oauth2DeleteScopeMapOpt),
|
DeleteScopeMap(Oauth2DeleteScopeMapOpt),
|
||||||
|
|
||||||
|
|
@ -666,7 +666,7 @@ pub enum Oauth2Opt {
|
||||||
SetLandingUrl {
|
SetLandingUrl {
|
||||||
#[clap(flatten)]
|
#[clap(flatten)]
|
||||||
nopt: Named,
|
nopt: Named,
|
||||||
#[clap(name = "landing_url")]
|
#[clap(name = "landing-url")]
|
||||||
url: String,
|
url: String,
|
||||||
},
|
},
|
||||||
#[clap(name = "enable-pkce")]
|
#[clap(name = "enable-pkce")]
|
||||||
|
|
@ -696,7 +696,7 @@ pub enum Oauth2Opt {
|
||||||
pub struct OptSetDomainDisplayName {
|
pub struct OptSetDomainDisplayName {
|
||||||
#[clap(flatten)]
|
#[clap(flatten)]
|
||||||
copt: CommonOpt,
|
copt: CommonOpt,
|
||||||
#[clap(name = "new_display_Name")]
|
#[clap(name = "new-display-name")]
|
||||||
new_display_name: String,
|
new_display_name: String,
|
||||||
}
|
}
|
||||||
|
|
||||||
|
|
@ -732,13 +732,13 @@ pub enum PwBadlistOpt {
|
||||||
|
|
||||||
#[derive(Debug, Subcommand)]
|
#[derive(Debug, Subcommand)]
|
||||||
pub enum DomainOpt {
|
pub enum DomainOpt {
|
||||||
#[clap[name = "set_domain_display_name"]]
|
#[clap[name = "set-domain-display-name"]]
|
||||||
/// Set the domain display name
|
/// Set the domain display name
|
||||||
SetDomainDisplayName(OptSetDomainDisplayName),
|
SetDomainDisplayName(OptSetDomainDisplayName),
|
||||||
#[clap(name = "show")]
|
#[clap(name = "show")]
|
||||||
/// Show information about this system's domain
|
/// Show information about this system's domain
|
||||||
Show(CommonOpt),
|
Show(CommonOpt),
|
||||||
#[clap(name = "reset_token_key")]
|
#[clap(name = "reset-token-key")]
|
||||||
/// Reset this domain token signing key. This will cause all user sessions to be
|
/// Reset this domain token signing key. This will cause all user sessions to be
|
||||||
/// invalidated (logged out).
|
/// invalidated (logged out).
|
||||||
ResetTokenKey(CommonOpt),
|
ResetTokenKey(CommonOpt),
|
||||||
|
|
|
||||||
|
|
@ -45,7 +45,7 @@ struct RunOpt {
|
||||||
pub copt: CommonOpt,
|
pub copt: CommonOpt,
|
||||||
#[clap(name = "target")]
|
#[clap(name = "target")]
|
||||||
pub target: TargetOpt,
|
pub target: TargetOpt,
|
||||||
#[clap(name = "test_type")]
|
#[clap(name = "test-type")]
|
||||||
/// Which type of test to run against this system
|
/// Which type of test to run against this system
|
||||||
pub test_type: TestTypeOpt,
|
pub test_type: TestTypeOpt,
|
||||||
#[clap(parse(from_os_str), short, long = "profile")]
|
#[clap(parse(from_os_str), short, long = "profile")]
|
||||||
|
|
@ -65,7 +65,7 @@ pub(crate) enum TargetOpt {
|
||||||
#[clap(name = "kanidm")]
|
#[clap(name = "kanidm")]
|
||||||
/// Run against the kanidm http profile
|
/// Run against the kanidm http profile
|
||||||
Kanidm,
|
Kanidm,
|
||||||
#[clap(name = "kanidm_ldap")]
|
#[clap(name = "kanidm-ldap")]
|
||||||
/// Run against the kanidm ldap profile
|
/// Run against the kanidm ldap profile
|
||||||
KanidmLdap,
|
KanidmLdap,
|
||||||
}
|
}
|
||||||
|
|
@ -78,8 +78,8 @@ impl FromStr for TargetOpt {
|
||||||
"ds" => Ok(TargetOpt::Ds),
|
"ds" => Ok(TargetOpt::Ds),
|
||||||
"ipa" => Ok(TargetOpt::Ipa),
|
"ipa" => Ok(TargetOpt::Ipa),
|
||||||
"kanidm" => Ok(TargetOpt::Kanidm),
|
"kanidm" => Ok(TargetOpt::Kanidm),
|
||||||
"kanidm_ldap" => Ok(TargetOpt::KanidmLdap),
|
"kanidm-ldap" => Ok(TargetOpt::KanidmLdap),
|
||||||
_ => Err("Invalid target type. Must be ds, ipa, kanidm, or kanidm_ldap"),
|
_ => Err("Invalid target type. Must be ds, ipa, kanidm, or kanidm-ldap"),
|
||||||
}
|
}
|
||||||
}
|
}
|
||||||
}
|
}
|
||||||
|
|
|
||||||
Loading…
Reference in a new issue